In brief ⚡
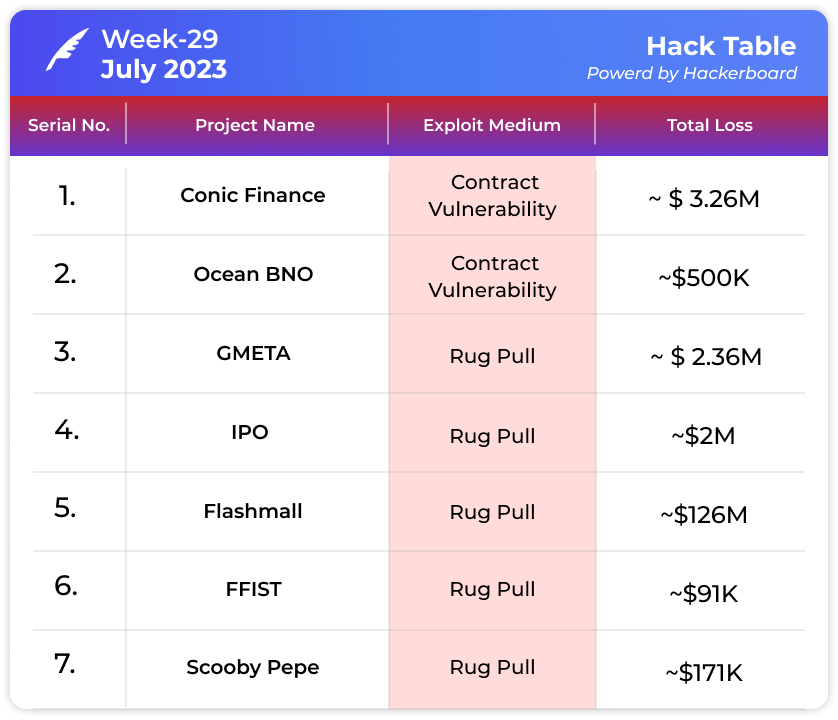
😮 Conic Finance DeFi Project Plagued by Exploits, Loses $4.1 Million in Double Hack: $3.2 Million from ETH Pool and $934,000 from crvUSD Pool
🔒 Exploit Strikes BNO on BSC: $500K Loss Due to Incorrect Reward Calculation, EmergencyWithdraw Function Vulnerability.
😱 A series of Rug Pulls happened within the span of four days. Tokens like GMETA, IPO, Flashmall, FFIST and ScoobyPepe were affected
Hacks and Scams⚠️
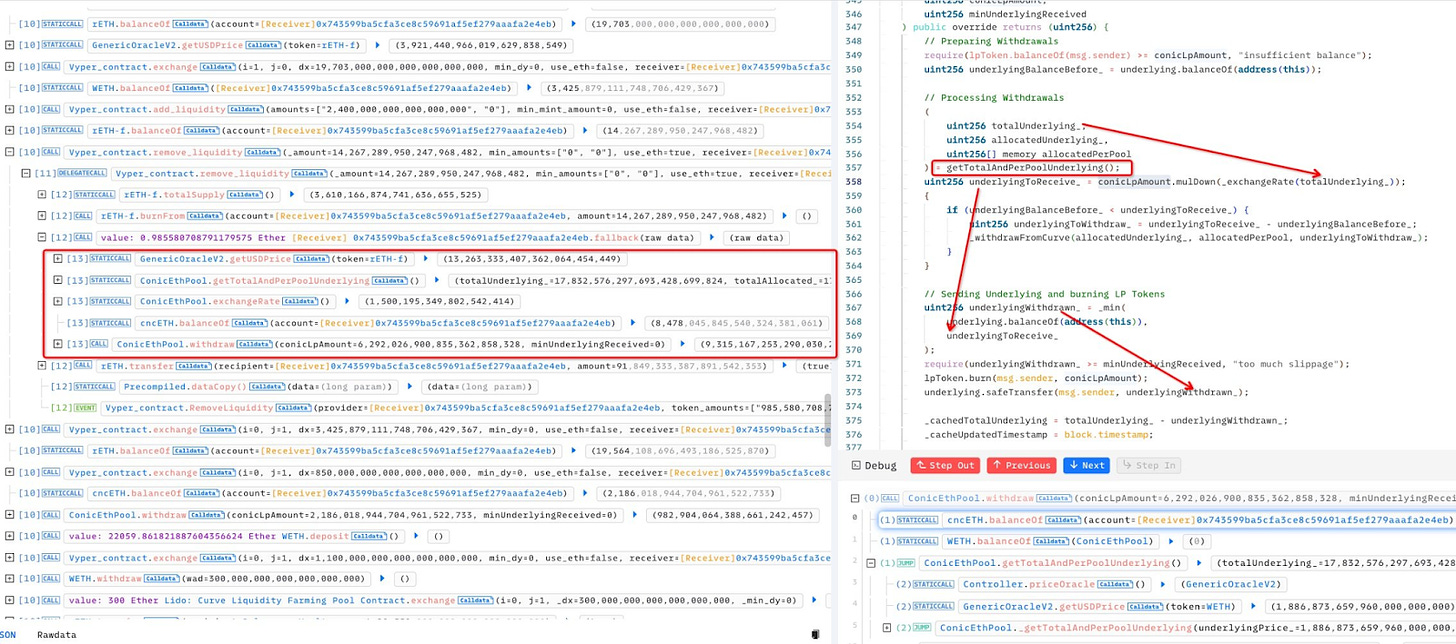
Conic Finance
Amount of Loss: ~ $3.26 Million
Analysis
Conic Finance DeFi project faced a re-entrancy vulnerability, resulting in the theft of 1,700 ETH, equivalent to approximately $3.22 million, from the project's ETH pool.
The project promptly disabled deposits on its front-end and initiated efforts to patch the vulnerable smart contract.
In an attempt to communicate with the attacker, the Conic Finance team sent a message via the blockchain, inquiring about the possibility of discussing potential next steps.
Despite assurances that the first incident was limited to the ETH pool and other pools were safe, Conic Finance suffered a second hack shortly after the initial exploit.
The attacker targeted the crvUSD pool, managing to steal around $934,000, but could only realize approximately $300,000 in profit from the second hack.
Ocean BNO
Amount of Loss ~ $500k
Analysis
Ocean BNO on Binance Smart Chain (BSC) suffered a $500K attack on July 18, 2023.
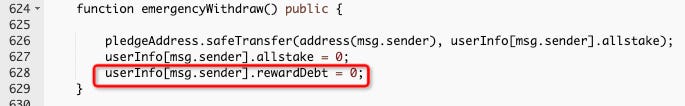
The attack exploited a smart contract vulnerability related to incorrect reward calculations for NFT and ERC20 token stakes.
The attacker utilized the emergencyWithdraw function, which failed to process NFT stake records and set rewardDebt to 0.
By withdrawing NFT stakes, the attacker could bypass the reward calculation check and profit from the exploit.
The attacker repeated the process multiple times and converted the rewards into BUSD tokens.
GMETA
Amount of Loss ~ $2.36 Million
Analysis
GMETA on BSC experienced a rug pull, resulting in a loss of approximately $2.36 million and a significant price drop of -96%.
The contract creator transferred 1 million $GMETA tokens to another address and used 120,000 GMETA tokens to swap out 2,367,507 USDT, causing price slippage.
Consequently, only 1 million USDT remained in the pair after the exploit.
Currently, another address distributes the remaining $1 million+ USDT to multiple addresses in smaller amounts.
IPO
Amount of Loss ~ $ 2 Million
Analysis
The scammer's tactic involved modifying the router address of another contract to execute the attack and bypass the burnToken() function judgment.
Flashmall
Amount of Loss ~ $ 550k
Analysis
Flashmall on the BNB chain experienced a rug pull, resulting in a loss of approximately $550k.
The scam involved the privileged address, set by the project, manipulating the setPointRate function.
The attacker (0x613c6....193a) exploited the vulnerability by minting the tokens 10 times in each iteration and performing a 1:1 swap back of the tokens.
Ultimately, the attacker removed liquidity from the project, resulting in a profit of $550k, which was subsequently sent to Tornado Cash.
FFISTR
Amount of Loss ~ $ 91k
Analysis
FIRE FIST $FFIST on the BNB Chain suffered exploitation resulting in a $91k profit for the attacker.
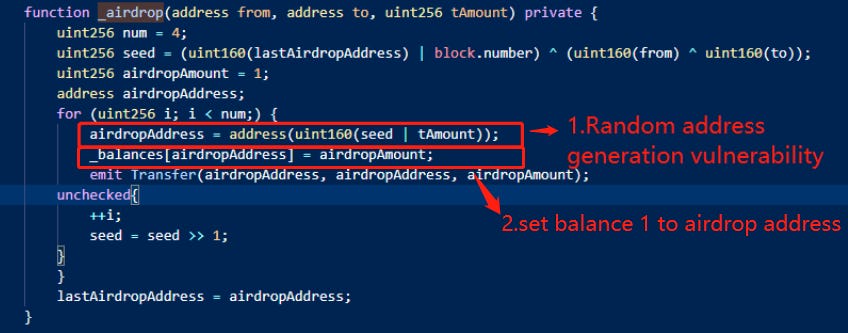
The exploit involved the _airdrop function within the transfer() mechanism, designed to distribute $FFIST to random addresses.
However, the random addresses could be predicted due to manipulable parameters such as the last airdrop address, block number, and from & to addresses.
Additionally, the number of tokens airdropped to an address was set to one token rather than incrementing by one. This created an imbalance in the pool, allowing a small amount of $FFIST to be exchanged for a significant amount of USD.
Scooby Pepe
Amount of Loss
Analysis ~ $ 171k
Scooby Pepe token ($SCO) on the Ethereum blockchain experienced a rug pull resulting in a loss of 90 ETH, equivalent to approximately $171k.
The exploit involved the contract with the address 0x8e2aada8069c2FcE1139dE697870E83f4145A8Ab.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
Crypto bridges sins exposed. Exploiting weak spots of multi-chain protocols.
The article identifies vulnerabilities in smart contract bridges used in blockchain protocols. These include miscalculating gas execution fees leading to potential DoS attacks, not accounting for gas usage on destination chains, and return bombs causing Out Of Gas errors. The author also highlights issues with handling errors, state finality, reorgs, and trust assumptions in bridges. Lastly, the article discusses the problems with different types of token transfers and the potential for exploits due to EVM differences across chains.
Decoding Ocean BNO’s $500k Exploit
On the 11th of July 2023, the Rodeo Finance on the Arbitrumchain was attacked. The attack was made possible by a Price Oracle Manipulation vulnerability. And around 472ETH was stolen by the hackers from the exploit.
Web3 Community Spotlight🔦
We are Sponsors for the "PARUL LET'S HACK" Hackathon, supported by @Azure @quine_sh @devfolio @ParulUniversity!
Participants will receive special grants, prizes and opportunities @QuillAudits
Use the link below to register and hack together, parulletshack.devfolio.co
Thanks for reading HashingBits! Share a summary of our newsletter on your social media platforms, tag us, and use the #AwareToEarn hashtag, and you could win 10 USDT as a reward! Help us build a safer Web3 ecosystem and have a chance to earn rewards and support our work.