In brief⚡
Events Under the Spotlight💥
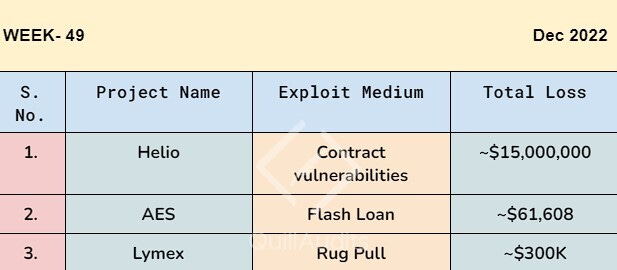
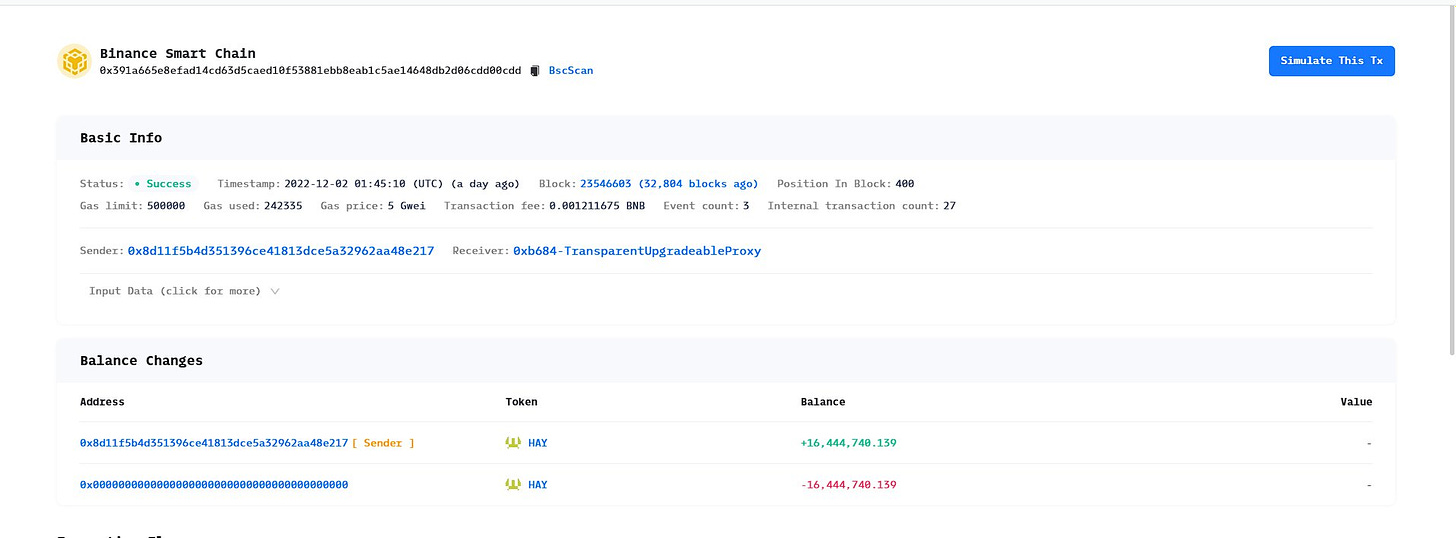
Helio Protocol Exploited for $15M after Ankr Exploit
The Helio exploit came just hours after the $5 million DeFi Ankr was attacked. The Ankr attacker created 6 quadrillion aBNBc tokens, which they later converted into approximately 5 million USDC.
The Ankr exploit caused the price of aBNBc tokens to drop by 99% in the minutes following the attack, laying the groundwork for the second Helio exploit.
Exploiters piggyback on a previous attack due to a delay in updating price data on BNB-related derivative tokens.
The $HAY was then exchanged for approximately $15 million in $BUSD stablecoin by the attackers.
Lymex Lost $300,000 in a Rug Pull.
The
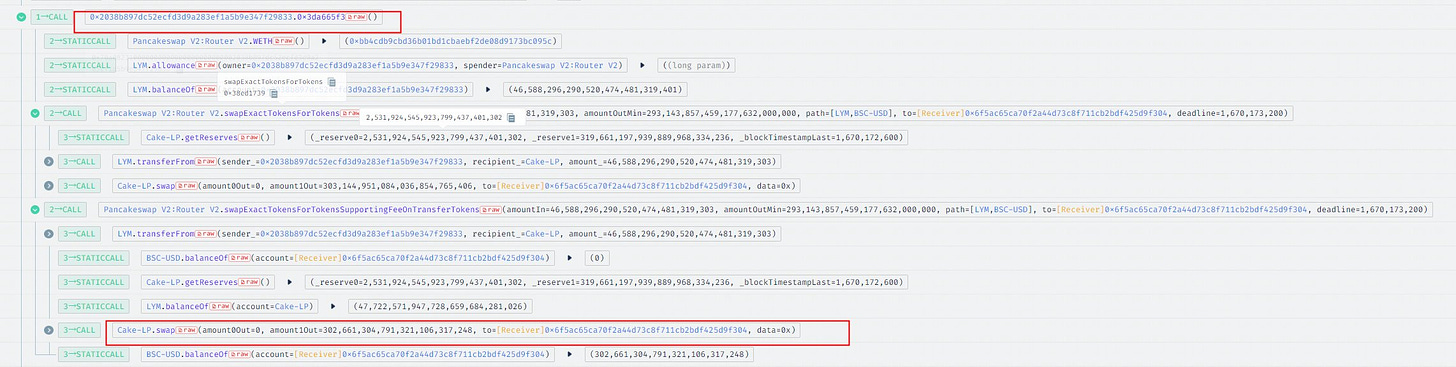
0xbC8054Ab4Bb4E60a13eDE09854F7957FF16D9679whitelist address transferred 46,633,195 $LYM to the0x00e6392f9ae5d022e30ff406830bb9b3bed6993eaddress.8 days ago, the
0x00e639address approved the maximum amount of LYM transfer.The $LYM were then transferred to Contract 2 (
0x2038b897), which swapped out 302,661 $BUSD.The $BUSD was sent to the deployer, and the address
0x92c2eA2F.
Flash Loan Attack Caused AES ~$61K
The attacker first transfers some $AES into pair, creating an unbalanced supply, and then employs the skim function to send excess tokens to the hacker's specified address.
The skim function balances the supply of pairs and sends any leftover funds to the specified address.
The attacker specifies the pair contract as the receiving address here, causing the excess $AES to be sent to the pair contract once more, leaving the pair contract unbalanced after forced balancing.
If the sender is the pair contract, part $AES will be burned when calling the transfer function (similar to deflationary).
$AES is burned to a small amount through repeated forced balancing operations, allowing a small amount of $AES to be swapped for a large amount.