In brief⚡
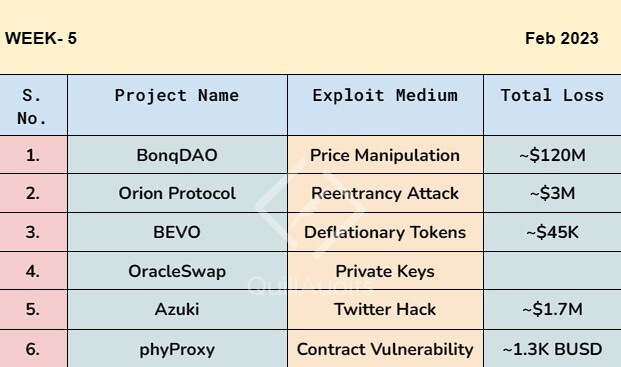
Events Under the Spotlight💥
🤯BonqDAO was exploited for ~$120 million.
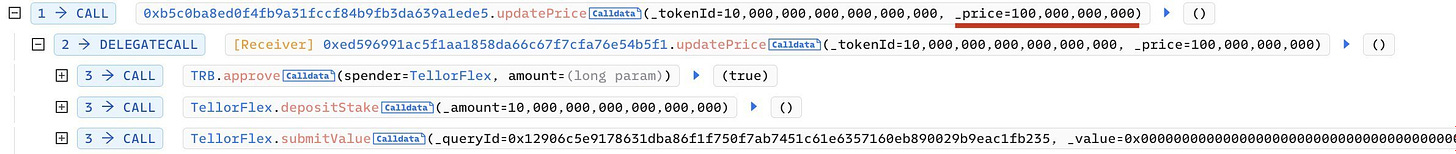
BonqDAO on Polygon was hacked due to faulty logic in calculating the WALBT token price.
The attacker staked a small amount of TRB tokens and then used TellorPriceFeed to update the WALBT token price (0x8f55).
Following the initial funding from Ethereum, the attacker borrowed more $BEUR tokens at a high token price and then liquidated more $WALBT tokens at a low token price.
The hacker converted approximately $1.2 million in stolen tokens into ETH and stablecoins. During the exploit, approximately 114 million walbt, AllianceBlock's wrapped native token, were stolen.
Orion Protocol has lost $3 million in cryptocurrency due to a trading pool exploit.
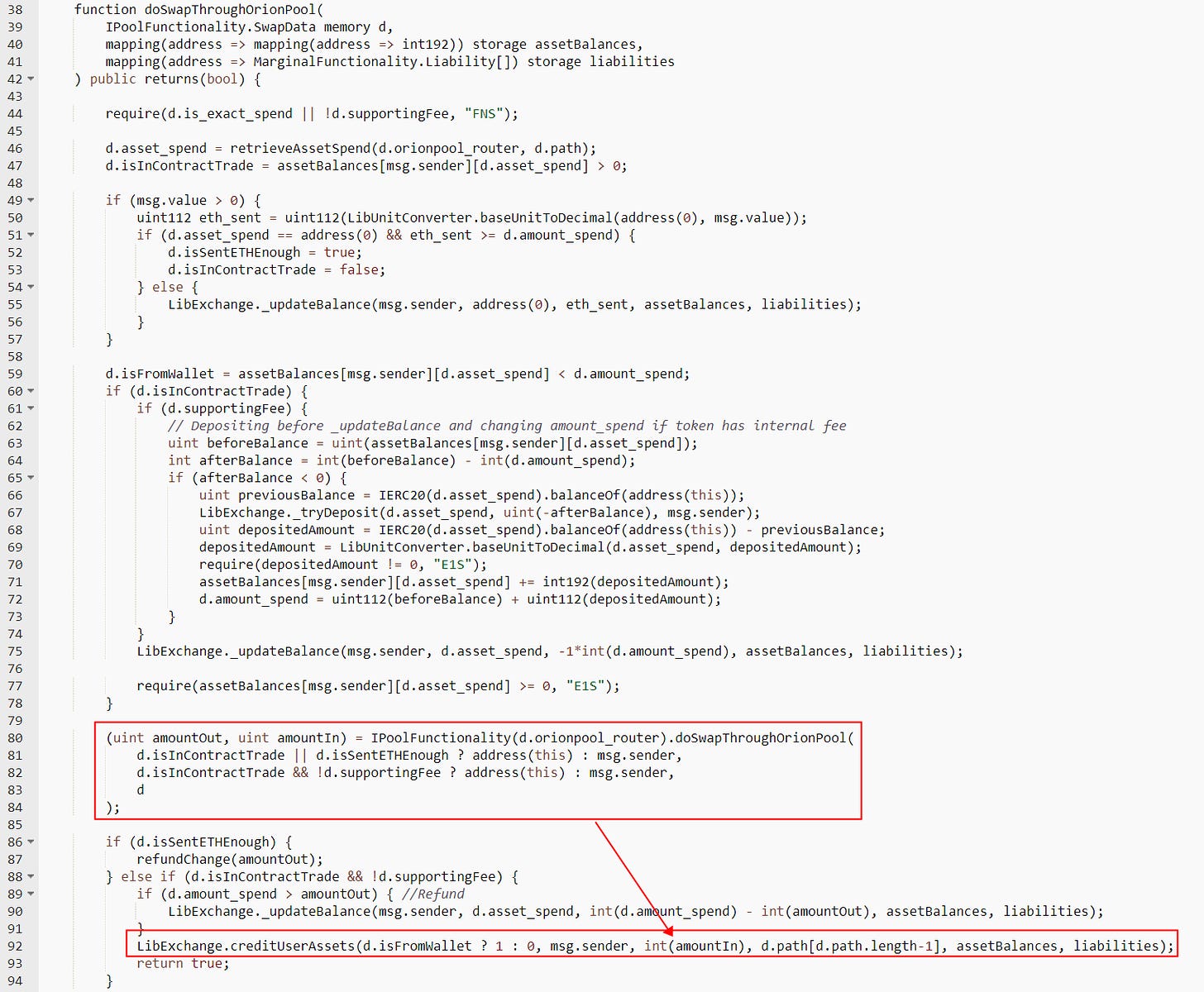
Orion was the victim of a reentrancy attack, which occurs when an attacker repeatedly withdraws funds from a smart contract. The root cause is a reentrancy problem in the PoolFunctionality.
The asset (i.e., USDT) balance is miscalculated due to the _doSwapTokens function.
The miscalculated amountOut in the PoolFunctionality. doSwapTokens function, in particular, will eventually lead to the amountIn argument passed into the LibExchange.creditUserAssets function.
The asset (i.e., USDT) balance needs to be corrected in this function.
Finally, the attacker withdrew 5,689,532 USDT, returned 2,853,326 USDT, and exchanged the remaining USDT for 1,651 WETH as profit.
On-chain sleuths estimated the losses at $2.8 million for Orion's Ethereum implementation and $200,000 for its BSC implementation. Shortly after the event, an attacker-identified wallet began passing ether tokens through the privacy mixer Tornado Cash.
BonqDAO on Polygon was attacked due to the flawed price oracle it relies on.
The BEVO NFT Art Token (BEVO) on BSC was hacked, resulting in a loss of approximately $45,000.
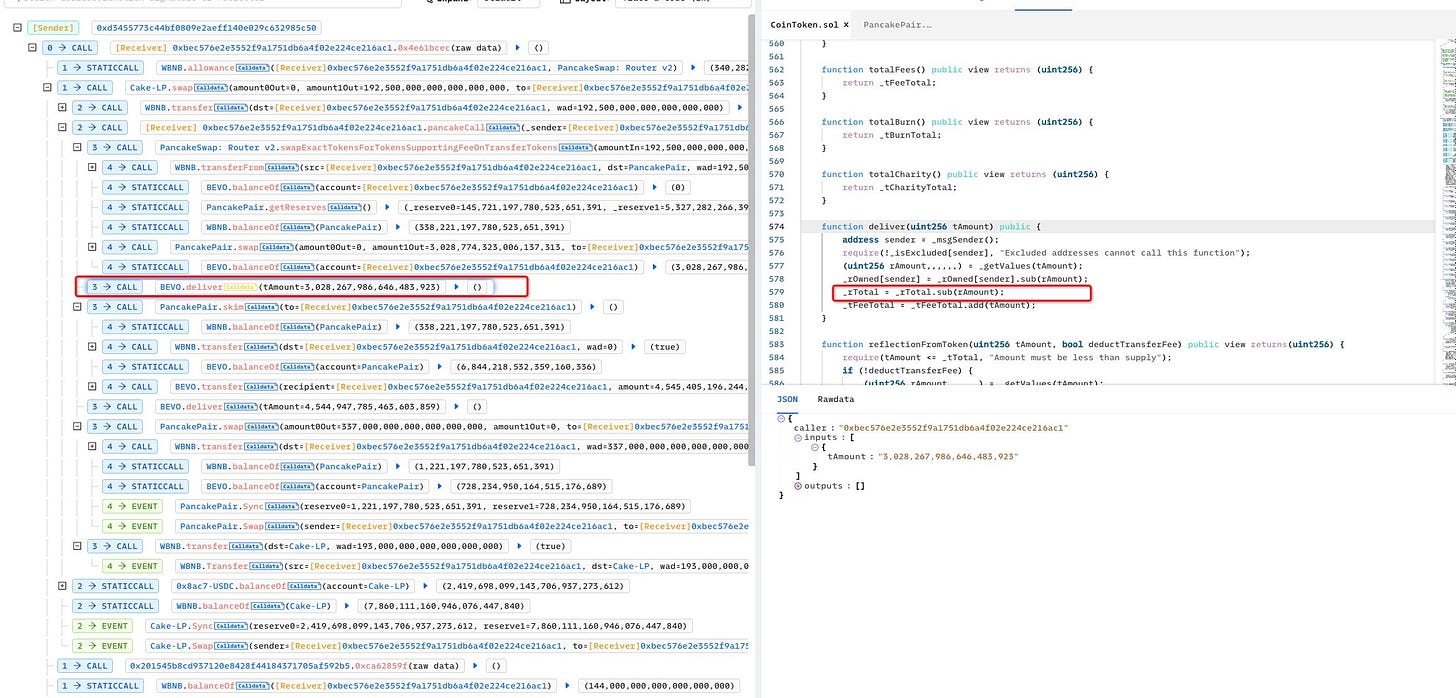
Because BEVO is a deflationary token, when the attacker calls the function deliver(), the value of _rTotal decreases, affecting the return value of getRate(), which is used to calculate the balance.
After manipulating the token balance, the attacker invokes the function skim to transfer the increased PancakePair balance to his account.
Finally, the attacker invokes the function deliver() once more and returns the increased BEVO to WBNB.
OracleSwap was hacked as its private key got exposed
OracleSwap, a Songbird Network DEX protocol, has suspended operations due to compromising its private keys.
FlareMetrics has advised OracleSwap delegates to switch to other FTSO operators and revoke access due to the risk of stealing their rewards from bad actors.
OracleSwap intends to launch a new FTSO infrastructure with new addresses once the improvement proposals are implemented.
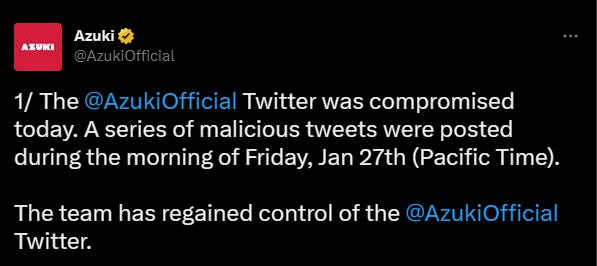
AzukiOfficial Twitter got compromised
The NFT project Azuki confirmed that its Twitter account had been hacked and that the team had regained control of the account.
Hackers posted two tweets on Azuki's Twitter account, one of which was pinned to the top, encouraging users to claim the virtual land.
Azuki officials warn users to be wary of this scam and to avoid clicking on any links.
Amont lost to twitter hack is approximately ~1.74 million
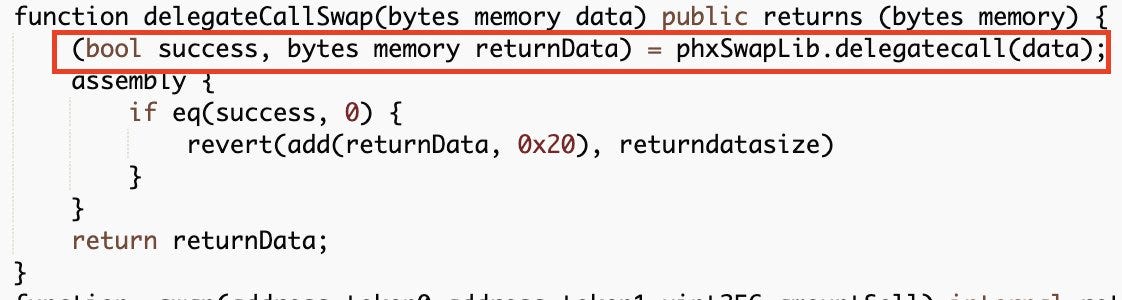
phyProxy on BSC lost ~1.2K BUSD due to recent exploit.
BSC's phyProxy was attacked, resulting in a loss of 1.2K BUSD.
The root cause is a forced investment caused by unverified delegate calls in the public delegateCallSwap function.
To profit, the attacker first created a worthless BUSD/FakeToken(0x890a) pair in Pancakeswap, then forced phxProxy to buy the FakeToken with $BUSD, and finally removed all liquidities.