In brief⚡
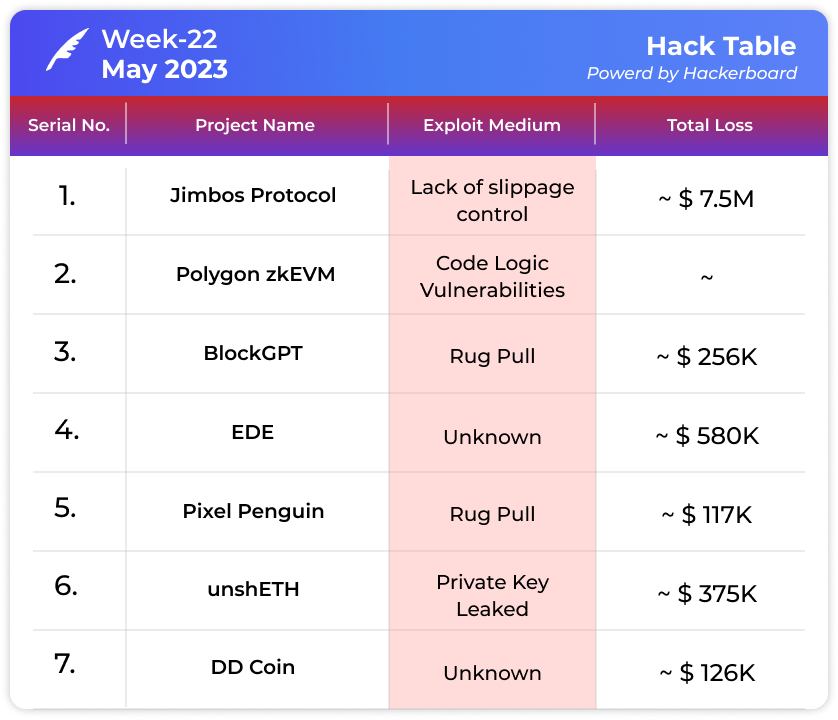
💸 Jimbos Protocol's Wallet Takes a $7.5M Hit!
💥Polygon zkEVM Unmasked! Code Logic Vulnerabilities Exposed!
😈BlockGPT Rug Pull Scam: Hackers Laughing all the Way to the Bank with $256K!
💔 EDE Loses $580K to Scammers: When Trust Turns into Betrayal!
🐧 Pixel Penguin Investors Burned! Rug Pull Results in $117K Loss!
Oops! UnshETH Happens: Loss of Private Key Costs $375K!
😱DD Coin Exploit: $126K Gone in the Blink of an Eye!
Hacks and Scams⚠️
Jimbos Protocol
Amount of Loss: ~ $7.5M
Analysis
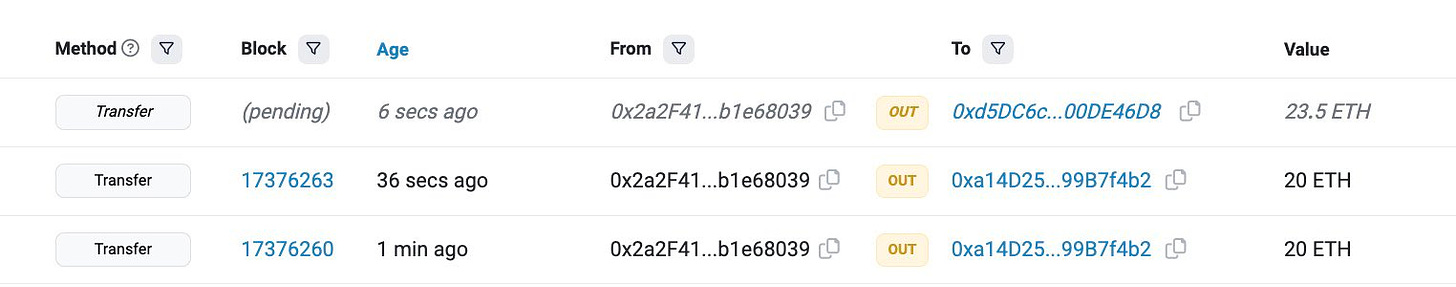
The Arbitrum ecological project Jimbos Protocol was attacked, and approximately 4,090 ETH (approximately $7.5 million) were stolen.
This attack occurred due to a lack of slippage control on the liquidity transfer operation.
This resulted in protocol-owned liquidity being invested in a skewed/imbalanced price range used in profit-making reverse swaps.
The hacker flash loans 10,000 WETH and exchanges it for $JIMBO to increase its value.
Then, 100 $JIMBO are transferred to the JimboController contract for later liquidity addition (because the JIMBO price is inflated, only a small amount of $JIMBO is required).
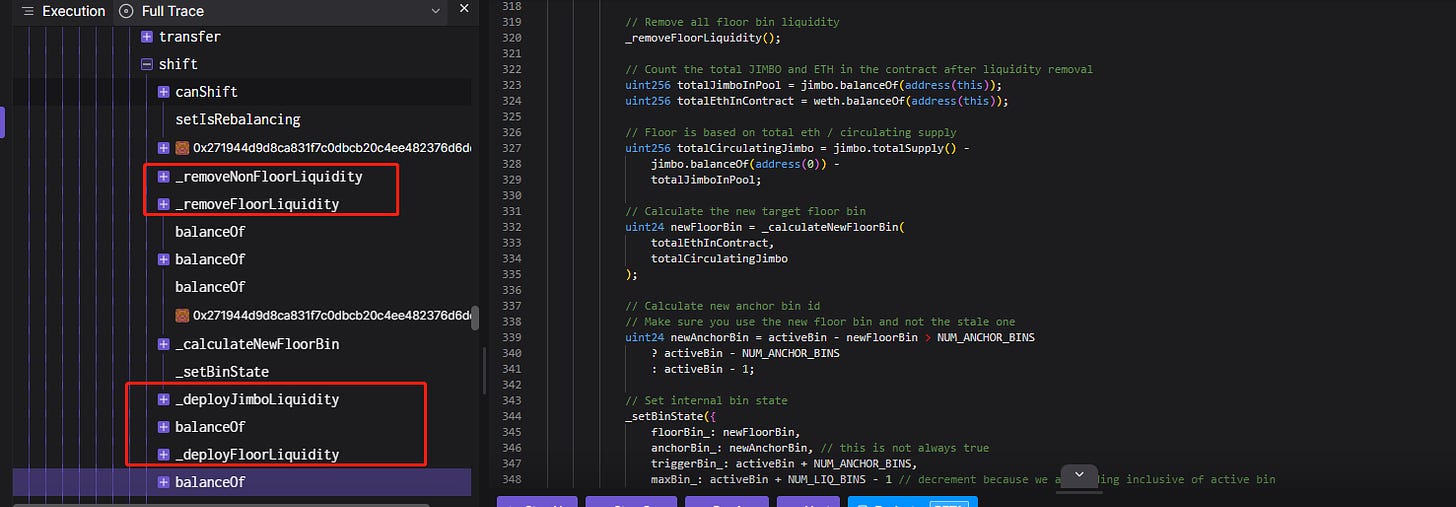
The attacker then invokes the shift function, allowing anyone to remove and replace the original liquidity with new liquidity. As a result, the JimboController contract's entire $WETH value will be added to the liquidity.
When adding liquidity, it uses the current price to calculate the required tokens, allowing the attacker to obtain more $WETH in an imbalanced situation.
Polygon zkEVM
Analysis
Blockchain security researcher iczc tweeted that a vulnerability in Polygon zkEVM had been discovered and that he had received a bug bounty from Immunefi L2.
Asset migration from L1 to L2 is hampered by the vulnerability, which prevents assets bridged from L1 to Polygon zkEVM (L2) from being properly claimed in L2.
In the code logic of processing claim tx pre-execution results, iczc discovered that malicious attackers can circumvent the "isReverted" pre-execution check on claim transactions by setting the gas fee to non-zero, allowing them to send a large number of Low-cost claims DoS attacks on sequencers and validators, increasing computational overhead.
Furthermore, after execution, transactions are not immediately removed from the pool.
The status is changed from Pending to Selected, and the record remains in the PostgreSQL database. There is currently only one trusted sequencer capable of retrieving and executing transactions from the transaction pool.
As a result, another vulnerability is that any deposit amount can be maliciously marked by sending a failed transaction. Because the credits have already been used, claim transactions that use them correctly will be rejected.
This renders the L2 network inaccessible to new users. With no funds at risk, the Polygon zkEVM team fixed this vulnerability by removing the specific gas logic for claiming transactions.
BlockGPT
Amount of Loss: ~ $256K
Analysis
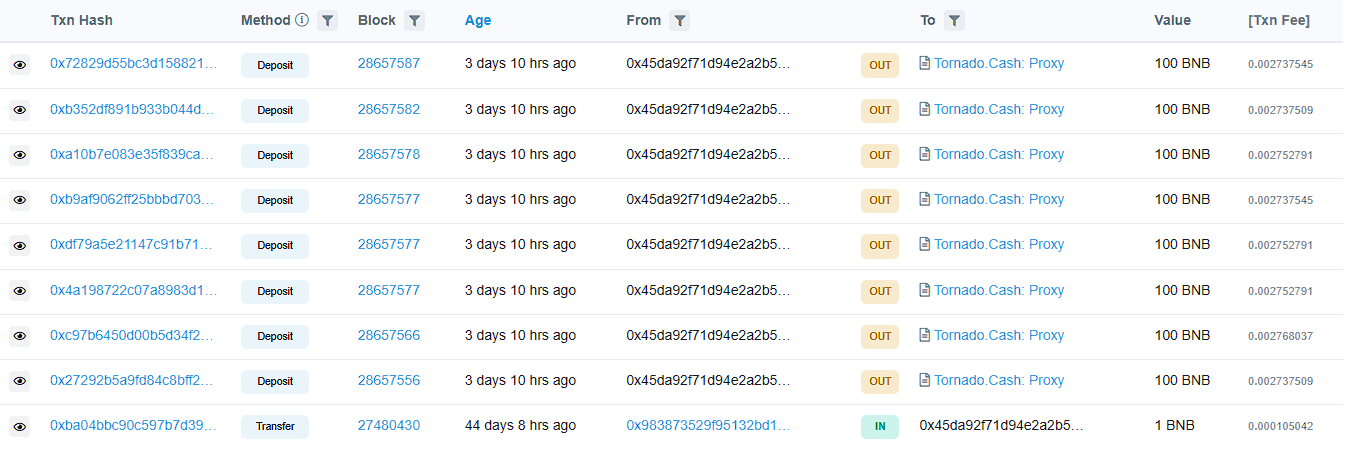
The Rug Pull of the BSC project BlockGPT occurred, involving assets worth over 816 BNB (approximately 256,000 USD), with 800 BNB transferred to Tornado Cash.
BGPT dropped by -52% within an hour of the exploit.
EDE
Amount of Loss: ~ $580K
Analysis
Perpetual DEX El Dorado Exchange (EDE) was allegedly attacked and lost approximately $580,000.
An address has been sending small amounts of money to Arbitrum's ELP-1 pool and withdrawing large sums.
The attacker has returned 334,000 USDC, according to monitoring.
Pixel Penguin
Amount of Loss: ~ $117K
Analysis
On-chain detective ZachXBT tweeted that a Rug Pull occurred on Pixel Penguin, a charity project created by Hopeexist1, which claimed to raise funds to help him fight cancer.
At present, the social accounts of Hopeexist1 and Pixel Penguin have been deleted, and the Pixel Penguin contract is worth only $117,000 (61.686 ETH).
unshETH
Amount of Loss: ~ $375K
Analysis
According to the LSDFi protocol unshETH, one of the unshETH contract's deployment private keys was leaked around 22:00 on May 31.
To be safe, the official has temporarily halted the withdrawal of unshETH's ETH.
The unshETH ETH deposit (TVL up to 35 million US dollars) is protected by multi-signature + time lock and is not at risk, according to the security model.
DD Coin
Amount of Loss: ~ $126K
Analysis
DD Coin was attacked and lost about 126,000 USDT.
The attacker initially received 1 BNB of funds from Tornado Cash about 17 days ago.
DD Coin has lost 21% following the attack.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
How to Identify and Mitigate Web3 Security Risks
Web3 security risks refer to the threats and vulnerabilities in the Web3 ecosystem. These risks revolve around smart contract vulnerabilities, phishing attacks, malicious code, social engineering attacks etc. When it comes to Web3 risk management, we need to be very much security oriented during the development phase; we prefer continuous monitoring more on the managing part later. Let’s first understand how the risks are identified.
Decoding Swaprum Finance $3 Million Rug Pull
On May 18, 2023, the deployer of Swaprum Finance, a decentralized finance platform on the Arbitrum chain, executed an exit scam (Rug Pull) and took around $3 million in user funds. They immediately deleted both their website and all of their social media profiles following the scam.
Web3 Community Spotlight🔦
Users can rent NFTs from the NFTBank. They have to pay a fixed commission when they want to get rent, and when they want to return NFT, the contract will take a second fee, depending on how many days you have NFT.
After ten days have passed, if you should hack the contract and finally have the NFT, the contract should not show that you have debt.