In brief⚡
Events Under the Spotlight💥
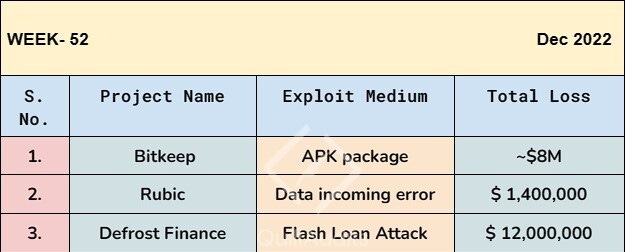
Hackers steal $8 million from Bitkeep wallets.
Several BitKeep cryptocurrency wallet users reported that their wallets were emptied during Christmas after hackers triggered transactions that did not require verification.
The attacker set up several fake websites for BitKeep users to update their wallet apps to the most recent versions.
Unknown to the victims, the APK file downloaded from the site was a malicious file designed to steal unsuspecting users' seed phrases.
Those who downloaded the trojanized APK package are advised to transfer all funds to the official store after downloading the official apps from Google Play or App Store, create a new wallet address, and transfer all funds.
The platform advises that any wallet addresses generated by the malicious APK should be considered compromised.
Rubic cross-chain exchange hacked, $1.4 million in user funds stolen.
After attackers gained access to the private keys of an administrator's wallet, they exploited Rubic, a service that allows users to swap cryptocurrencies between different exchanges.
On the Uniswap and PancakeSwap exchanges, approximately 34 million RBC and BRBC tokens were sold. As a result, Rubic continues to function normally, and all user funds are secure. There were no contracts exploited.
The attackers' 34 million RBC transfer was worth more than $1.2 million at the time of the hack.
Separately, the attacker's wallet, identified by Rubic in a tweet, held more than 205 BNB, or slightly more than $65,000, in a BNB Chain wallet and more than $205,000 in the ether in an Ethereum wallet.
Defrost Finance loses $12 million.
Another issue has arisen with the Avalanche ecological native stablecoin project's Defrost Finance protocol. The protocol was enhanced with fake mortgage tokens and malicious price oracles to liquidate current users.
The loss is estimated to be more than $12 million. Defrost Finance has officially stated that it has detected an emergency in V1 and that the team is investigating.
The attacker, according to analysis, changed the oracle's address using the setOracleAddress function, then used the joinAndMint function to mint 100,000,000 H20 tokens to the 0x6f31 address, and finally used the liquidate function to obtain a large amount of USDT using the false price oracle.