In brief⚡
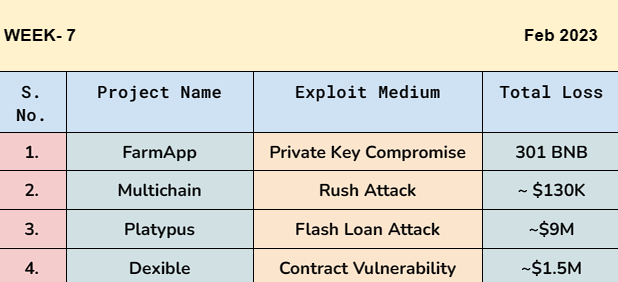
FarmApp lost 301 BNB due to a private key compromise.
Multichain's AnyswapV4Router contract suffered a rush attack.
Platypus project on AAVE protocol encountered a flash loan attack.
Dexible lost ~$1.54 million due to a contract vulnerability.
Hacks and Scams⚠️
FarmApp
Amount of Loss: 301 BNB
Analysis
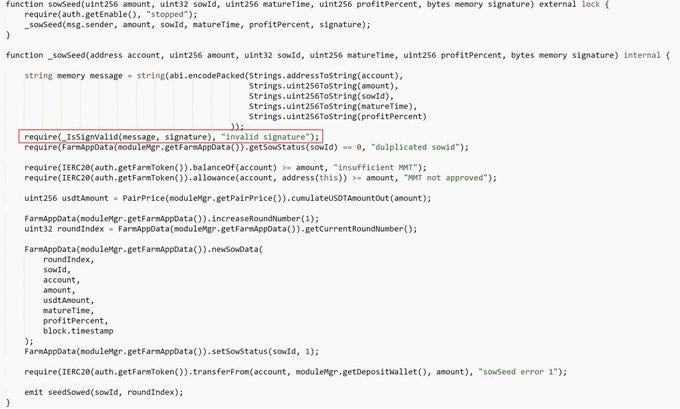
The private key for the FarmApp contract singer was stolen. The exploit brought in 301 BNB for the hacker.
Using the singer's signature, the attacker (0x2a45a576beecc945527a1b106c6d41d3ea52f9f7) called the sowSeed function to create newSowData with 42 sowid and then called the claimedSeed function once more to steal 936,387 $MMT.
The stolen MMT was transferred to the tornado cash after being exchanged for 301 BNB (roughly 93K USD).
The price of MmtMiner was down by 81% following the exploit.
Multichain
Amount of Loss: ~$130K
Analysis
Rush attack on Multichain's AnyswapV4Router contract resulted in a profit of about 87 Ethereum, or about $130,000, for the attacker.
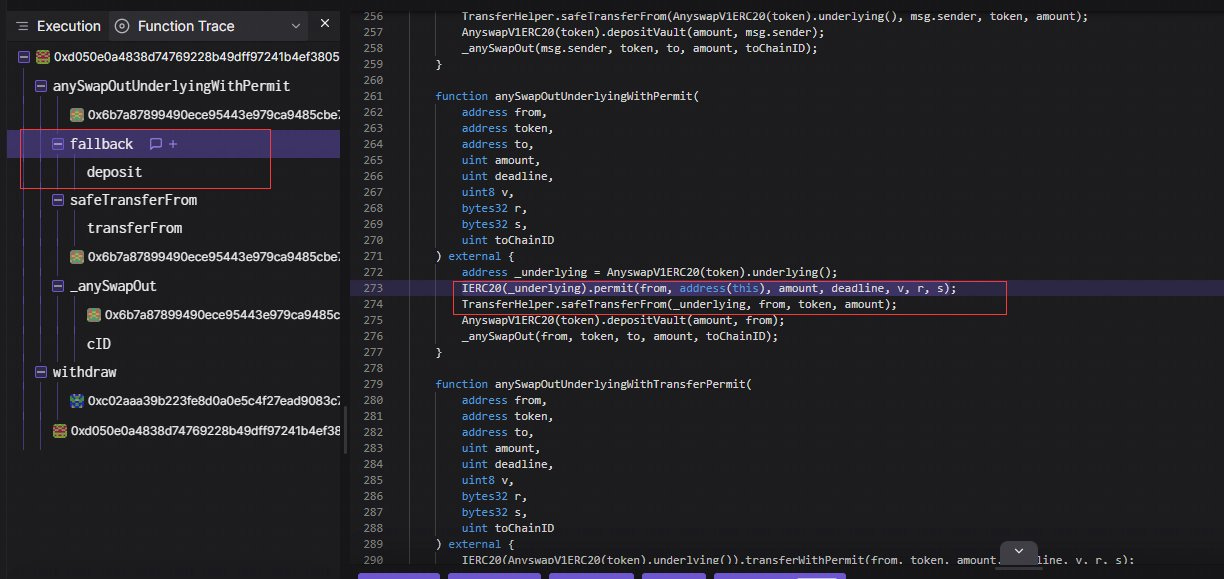
After analysis, it was discovered that the attacker preemptively called the
anySwapOutUnderlyingWithPermitfunction of theAnyswapV4Routercontract using the MEV contract (0xd050).Even though the function uses the permitted signature of the token verification and the stolen WETH this time does not have a relevant signature verification function and only activates a deposit function in a fallback.
The attacker can transfer WETH authorised by the _underlying address to attacked contract to the attack contract directly using the
safeTransferFromfunction in subsequent function calls without requiring signature verification.
Platypus
Amount of Loss: ~$9M
Analysis
A total loss of $9.05 million resulted from the exploitation of Platypus.
Although the project lost a lot of money as a result of the three attacks, the attacker only retained control of about $270,000 of that money. FixedFloat provided the initial funding for the exploiter.
The attacker first flash loans 44M $USDC, after which they use the Platypus contract's deposit function to create an equal number of LP-USDC.
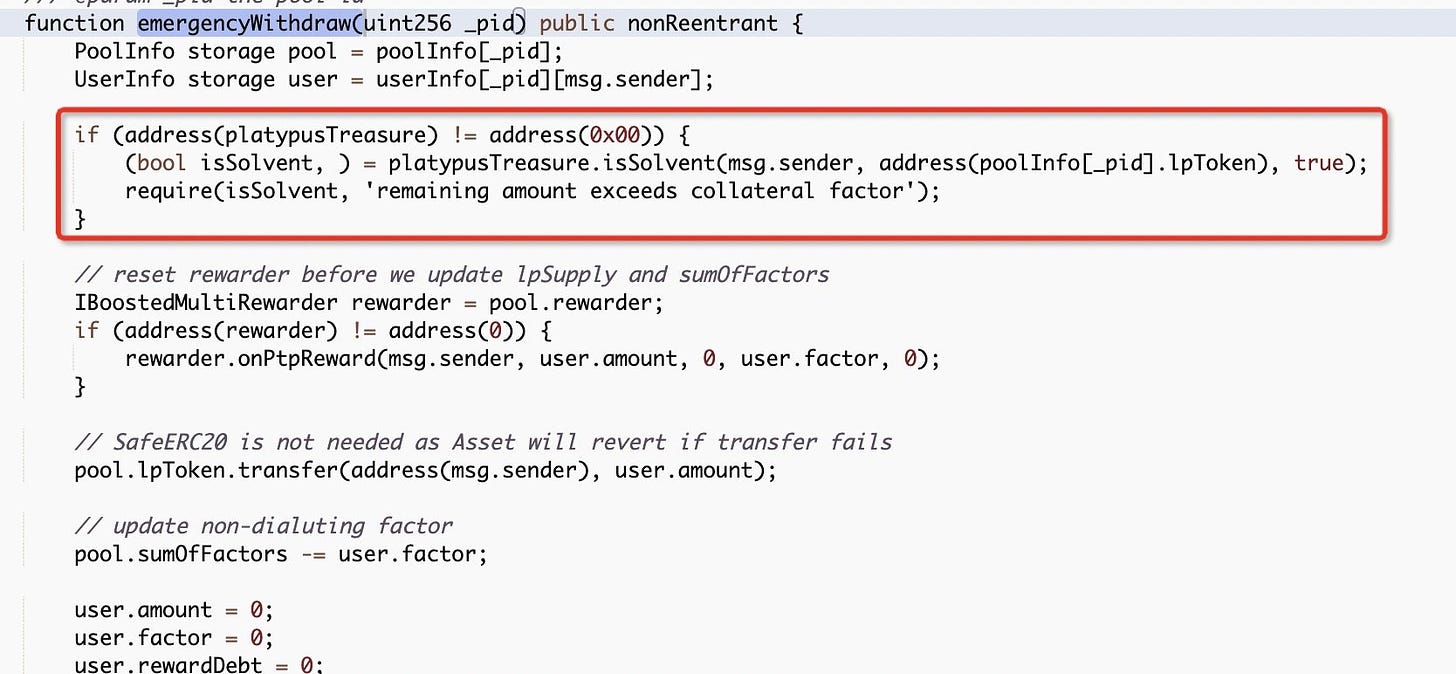
The weakness appears in the
emergencyWithdrawfunction's verification of theMasterPlatypusV4contract, which only fails when the amount of borrowed assets exceeds the borrowing limit.Regardless of the value of the user's borrowed assets, the function transfers all of the deposit assets.
Dexible
Amount of Loss: ~$1.54M
Analysis
A total loss of ~$1.54 million resulted from the exploitation of contract vulnerability from Dexible.
Users are urged to revoke permission for 0xde62e1b0edaa55aac5ffbe21984d321706418024 immediately.
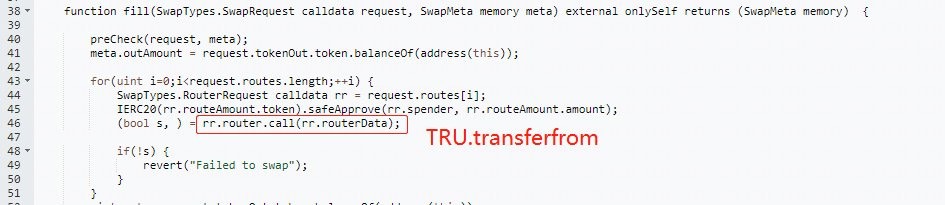
A logical flaw in the
selfSwapfunction causes it to call the fill function, which then calls hacker-defined data.By building a transfer from function in the data and passing other users' and his attack addresses, the hacker enables the transfer of tokens approved for the contract.
Only legitimate router addresses or whitelisted contracts should be passed in rr.router, according to the function. As a result, the attacker had access to ERC20 token contract addresses.
Users who authorised the transfer of tokens to the attacker through the DexibleProxy inadvertently approved the swap of those tokens.
EOA 0x6840 transferred 930 ETH and 1426 BNB to tornadocash.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
Web 3.0 and Cybersecurity – Short Paper
The Web 3.0 ecosystem is rapidly expanding, which raises additional security concerns. The read/write model of the Internet is gradually being replaced by the Web 3.0 model, a more recent model. Global businesses are investigating ways to incorporate web 3.0 into their operations.
The authentication and authorization area of security has undergone significant evolution over the past ten years. OAuth 2.0-based authentication is currently the accepted authentication protocol. This approach depends on a third-party provider of authentication services who has total access to user data and is free to filter or alter it as desired.
Testing and Formal Verification for Web3 Smart Contract Security
A skilled developer can use code to communicate the work to a machine. Still, occasionally a bug or a logical mistake in the code causes the device not to display the precise mechanism the developer had in mind.
Tune in to Engaging Twitter Spaces & Webinars! 🎙️
Web3 Community Spotlight🔦
QuillAudits is recognized as a partner of the Web3 Regulatory Sandbox, an initiative by Emerging Technologies Wing, Govt. of Telangana.


QuillCTF Panda Token Challenge is now accessible for developers to train their coding skills.


Innovations Unleashed: Stay Up-to-Date with Latest Product Launches🚀
We have launched QuillAcademy - a one-stop destination for learning advanced web3 security skills.
Here, we host sessions with leading auditors, run challenges, train developers through our fellowship, and publish in-depth post-mortem analyses of Web 3.0 hacks.