In brief⚡
Events Under the Spotlight💥
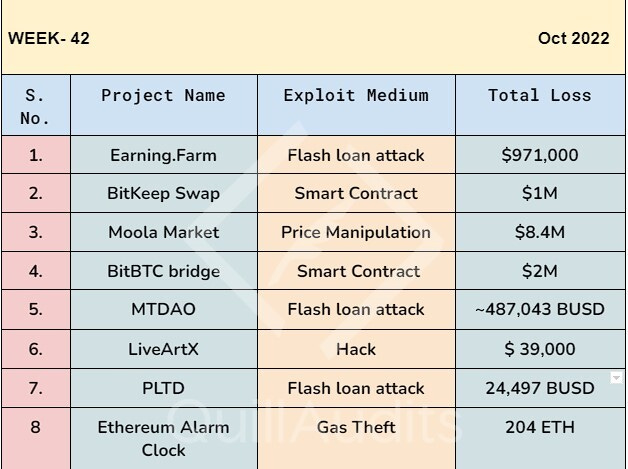
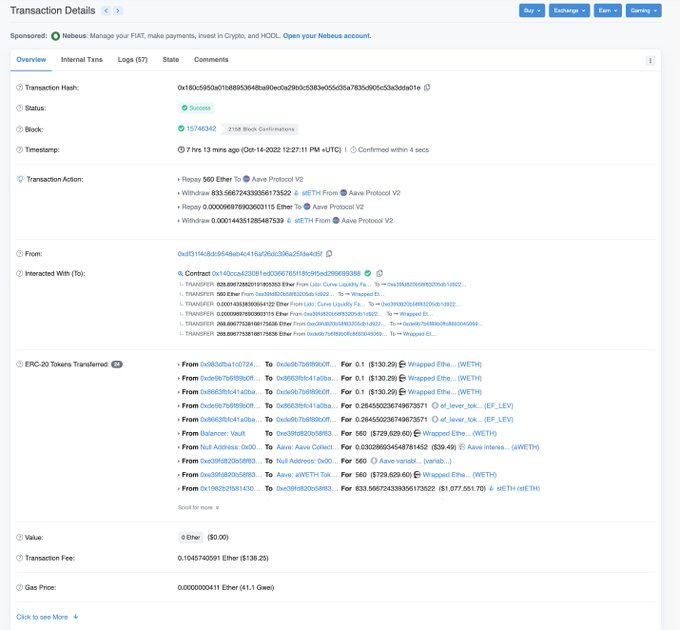
Earning.Farm lost $971,000 in a flash loan attack
As the project contract lacked a check that the protocol initiated a flash loan, the attacker was able to instruct the project to withdraw large sums of money, which they then transferred to themselves.
The attacker exploited this by making a small deposit followed by a large outside flash loan, causing the protocol to make a large withdrawal from eth to itself.
One of the hacker's transactions was front-run by the MEV bot 0xa57, which profited handsomely from the attack, earning 480 ETH ($623,000).
The second transaction was successful, and the attacker received 268 ETH ($348,000).
According to an MEV researcher, 0xa57 has been known to return funds obtained through a hack.
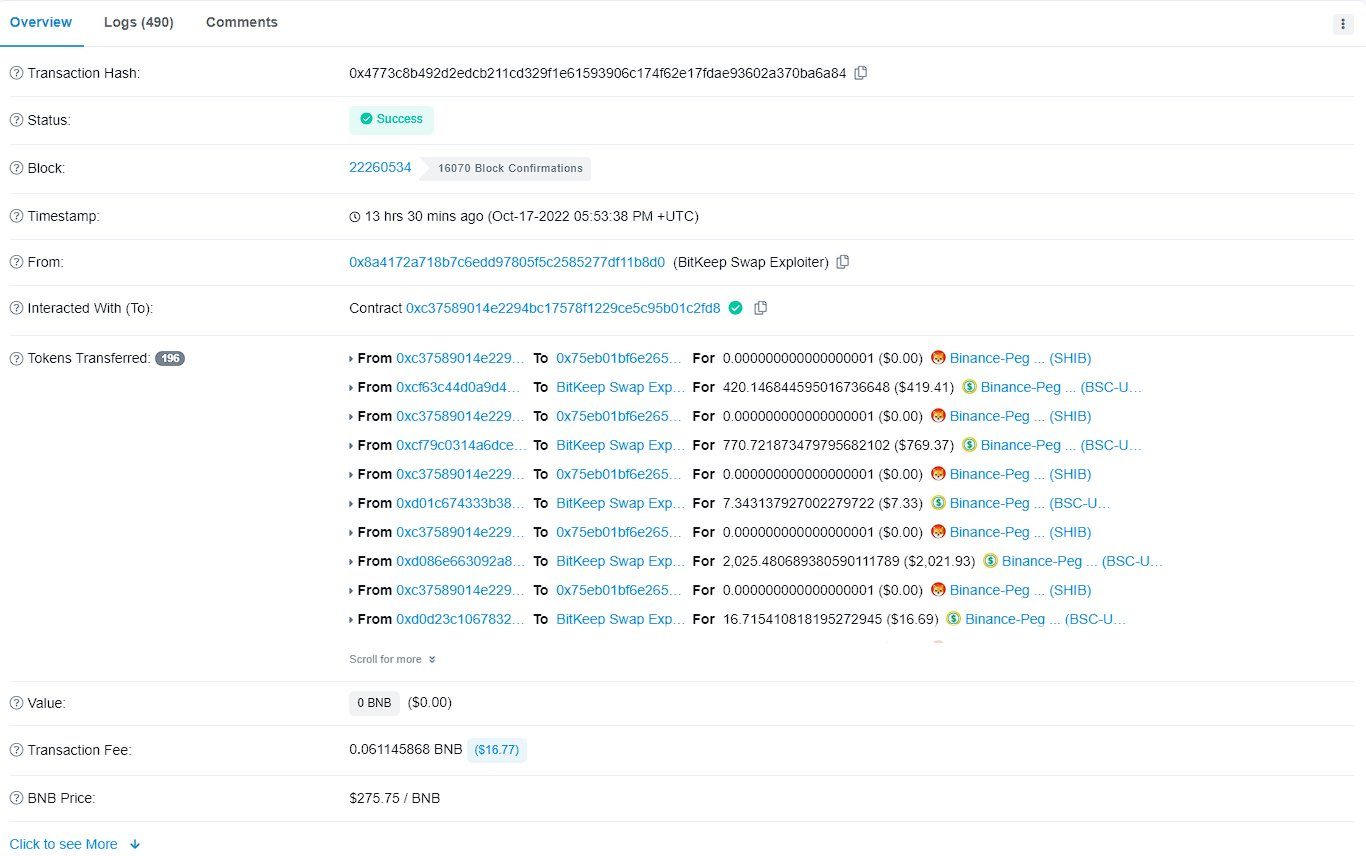
BitKeep Swap was hacked for over $1 million
The BitKeep crypto wallet's Swap feature was compromised, resulting in a hacker receiving more than $1 million in BNB.
A hacker used the swap feature to drain approximately $1 million from the BitKeep wallet.
The project acknowledged the error and promised to compensate those who were affected.
Moola Market exploited for $8.4 million
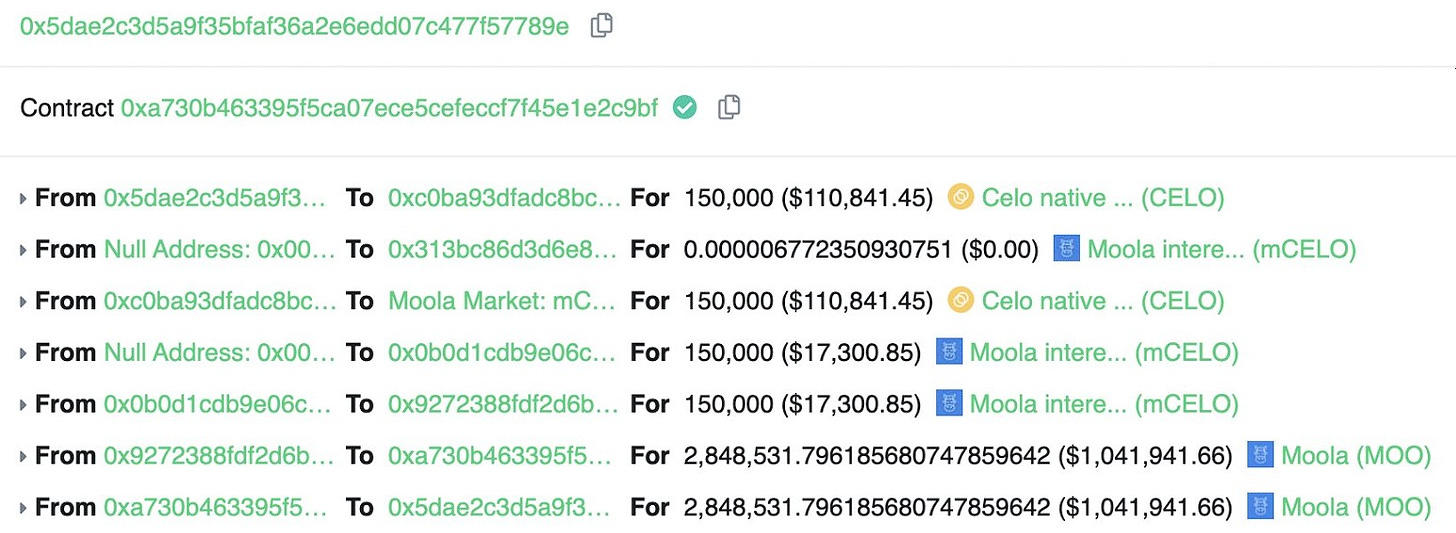
An attacker manipulated collateral prices to steal a collection of assets worth around $8.4 million from the Celo-based borrowing and lending platform, Moola Market.
To target the Moola Market, the exploiter obtained 243,000 CELO from Binance.
The attacker borrowed 1.8M MOO and lent Moola 60k CELO as collateral.
They started by increasing the MOO price with the remaining CELO and using it as collateral to borrow all other tokens.
The hacker garnered 1.8 million MOO tokens ($655,000).
They also received Celo-related tokens and stablecoins worth 8.8 million CELO ($6.5 million), 765,000 cEUR ($750,000), and 644,000 cUSD ($639,000).
In the end, the exploiter appears to have received 700,000 CELO as a 'bug bounty.'
They have attempted to migrate 50k of them to Impact Market's multi-signature.
Vulnerability in the BitBTC bridge to create 200 billion BitBTC tokens
@PlasmaPower0, a frustrated security researcher, reported on Twitter that "BitBTC's Optimism bridge is trivially vulnerable."


Following the Arbitrum tech lead's Twitter tweet, a bridge attacker generated 200 billion BitBTC coins.
However, it would take at least seven days to complete any transaction.
The development team for the BitBTC project, which a self-described "19-year-old Bitcoin believer founded,"; The company now has seven days to fix and remove the vulnerability.
Meanwhile, in an Ethereum transaction note, the hacker stated, "I'm not a hacker, simply want to test the vulnerability with a [proof of concept], won't touch any precious assets."
Metaverse DAO loses 487,042.615 BUSD in a flash loan attack
A flash loan attacked the MTDAO project party's unopened contract 0xFaC064847aB0Bb7ac9F30a1397BebcEdD4879841.
The hack affected the MT and ULM tokens, with a total profit of 487,042.615 BUSD.
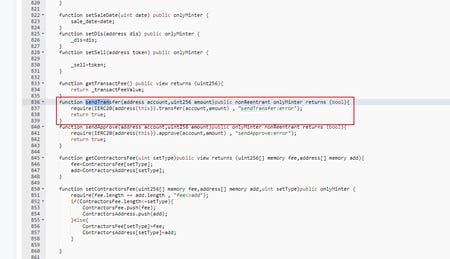
The attacker profited by calling the
sendtransferMT and ULM token contracts function using the functions 0xd672c6ce and 0x70d68294 in the unopened contract.
LiveArtX's Seven Treasuries NFT Collection exploited for $ 39,000
LiveArtX's official wallet was stolen, and several reserved NFTs were sold.
The attacker (0x5f78...A920) sent 7.3 ETH and 22.39 WETH to Bitkeep, then exchanged it for USDT and sent it to a new address (0x871e...A575).
The collection's price fell from 1 ether (ETH), or approximately $1,300, to 0.1 ether, or $130.
PLTD project lost 24,497 BUSD in a flash loan attack
The PLTD project was hacked, all BUSD in its trading pool were sold, and the hackers made 24,497 BUSD.
This attack primarily exploits code loopholes in the PLTD contract, uses a flash loan attack to reduce the PLTD token balance in Cake-LP (0x4397c7) to one, and then uses the PLTD to exchange all BUSD into the attack contract.
The attacker initiated two flash loan loans using the DODO protocol's flash loan and borrowed 666,000 BUSD as a reserve for the attack.
The attacker will exchange all 666,000 BUSD into 1.57 million PLTD tokens; at this time, the attacker already has a large number of PLTD tokens, which he will then use to manipulate the balance of PLTD tokens in Cake-LP.
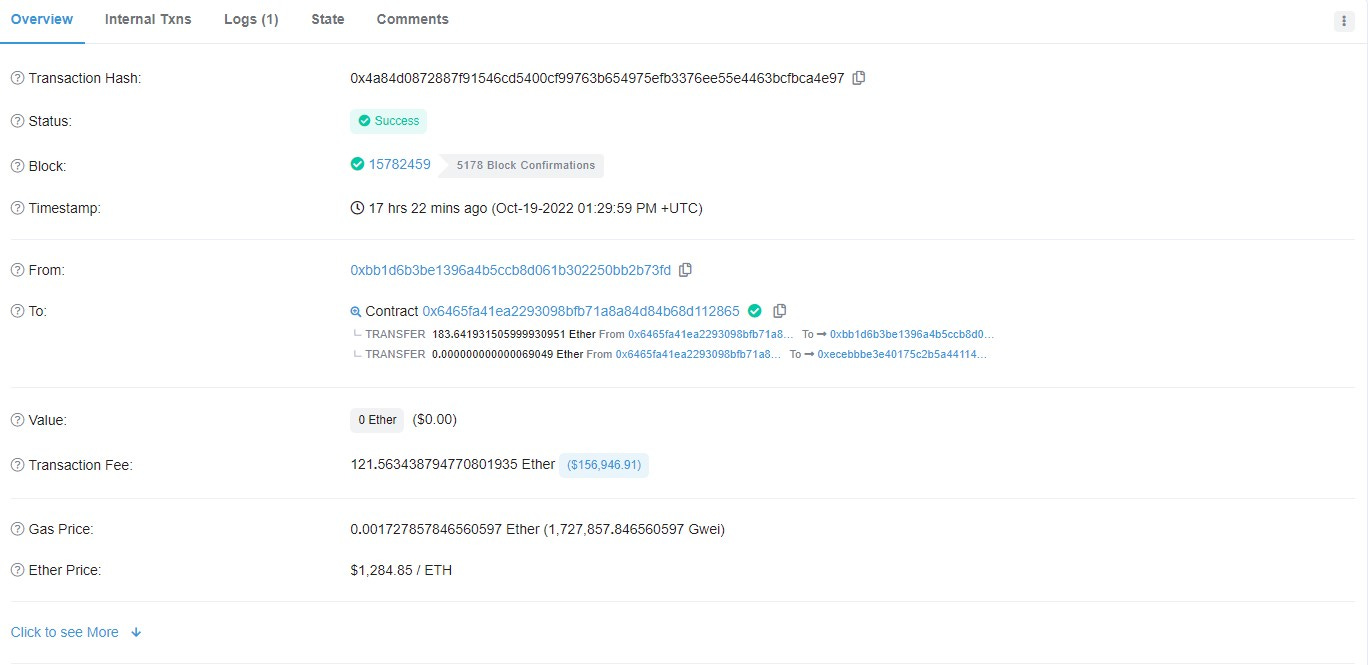
Hackers swept 204 ETH in gas fees from Ethereum Alarm Clock
Hackers manipulated the profit from returned gas fees from cancelled transactions due to a flaw in the scheduled transaction process.
The cancel function calculates and transfers the Transaction Fee (gas used * gas price) to the caller if the "gas used" exceeds 85000.
Exploiters used high gas prices to game the
TransactionRequestCorecontract, gaining a reward at the expense of the original owner.The miner receives 51% of the profit from the exploit, which explains why the MEV-Boost reward is so large.
Trending Blog of the Week🚀