🛑Hacking Heists: Hackers Got Away with ~$56.54M in the Second Week of April
HashingBits | Week- 15
In brief⚡
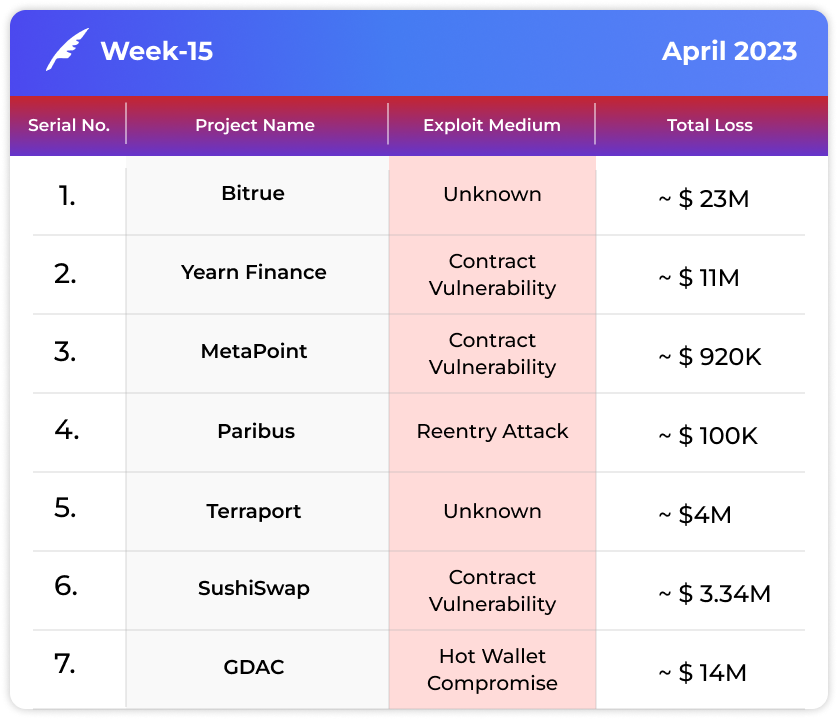
One of Bitrue's hot wallets was exploited for a whooping sum of ~$23M.
Yearn Finance lost ~$11M due to a smart contract vulnerability.
A vulnerability in the MetaPoint contract caused a loss of ~$920K.
Exploiters made away with ~$100K from a reentry attack on Paribus.
Terraport lost ~$4M in a recent exploit.
SushiSwap lost ~$3.34M due to contract vulnerability.
GDAC lost ~$14M to a hot wallet compromise.
Hacks and Scams⚠️
Bitrue
Amount of Loss: ~ $23M
Analysis
On April 14 2023, at 07:18 (UTC), Bitrue discovered a brief exploit in one of their hot wallets. Bitrue was able to address this issue quickly and prevent further financial exploitation.
The attackers withdrew approximately $23 million in ETH, QNT, GALA, SHIB, HOT, and MATIC.
Bitrue will temporarily suspend all withdrawals to conduct additional security checks before resuming withdrawals on April 18, 2023.
Yearn Finance
Amount of Loss: ~ $11M
Analysis
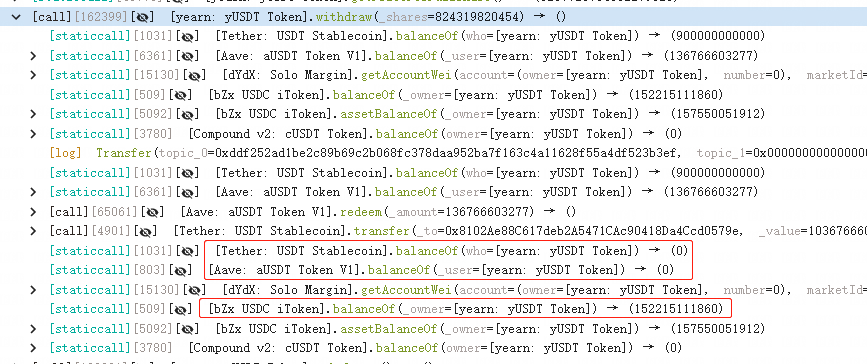
The root cause of the hack is a yUSDT Token contract misconfiguration.
The attacker used USDC to "consume" all of the USDT in the contract, causing the pool's balance to drop to zero and causing a large number of tokens to be minted.
The attacker initially flash loaned 5 million DAI, 5 million USDC, and 2 million USDT.
The hacker used the Aave contract's repayment function to repay other people's debts. This is done to reduce the collateral yield in the Aave pool, lowering its priority within the contract (the yield contract determines which pool to allocate funds to based on yield).
The hacker used the Yearn USDT Token contract's deposit function to deposit 900,000 USDT. Based on the deposit amount and the pool's token balances, this function minted a corresponding amount of yUSDT for the caller.
The contract held 1.18 million in funds, and the attacker owned a 90/103 share, which meant they could withdraw 1.03 million in funds.
MetaPoint
Amount of Loss: ~ $920K
Analysis
MetaPoint ($POT) on BNBCHAIN was compromised, resulting in a $920K loss.
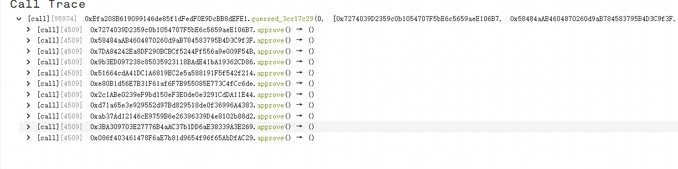
The root cause is that each time users deposit $POT, they will create a new contract to hold their funds, but the contract has a public approval function that will transfer all users' assets.
The attacker created attack contracts to bulk call this function and approved the maximum value.
Discovering the exploit, the project has locked the contract to avoid further losses.
Paribus
Amount of Loss: ~ $100K
Analysis
The total loss from the Paribus hack is $100,000.
The root cause is a known reentrancy problem in the old forked version of CompoundV2.
More about the reentrancy attack is below.
Terraport
Amount of Loss: ~ $4M
Analysis
Terraport, a decentralised finance project launched by TerraCVita, an independent Terra Classic development team, was hacked, and its liquidity was depleted.
According to data, nearly $4 million in LUNC, USTC, and TERRA tokens have been emptied.
In the first transaction, the attacker withdrew 9,148,426 TERRA and 15.1 billion LUNC, and in the second transaction, he withdrew 576,736 TERRA and 5,487,381 USTC.
Following both transactions, the Terraport smart contract now has a 2.8 million LUNC worth $362.
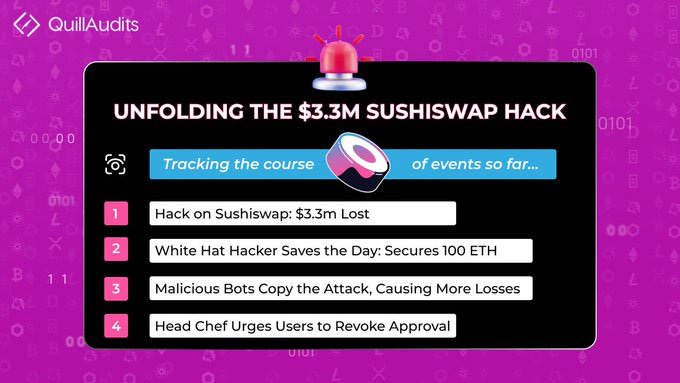
SushiSwap
Amount of Loss: ~ $3.34M
Analysis
SushiSwap was hacked on April 9, resulting in over $3 million in losses. SUSHI's RouteProcessor2 was attacked, resulting in a loss of approximately 1800 ETH, or $3.34 million.
The root cause is that ProcessRoute does not perform any checks on the user's route parameters, which allows the attacker to exploit this flaw to construct a malicious route parameter, allowing the attacker to create the Pool read by the contract.
The losses were recovered using a white hat security procedure, and the hacker returned a significant portion of the stolen funds.
Chef Nomi, the protocol's creator, was subpoenaed by the SEC just a day before the hack. However, the hack did not prevent the community from working together to resolve the issue.
GDAC
Amount of Loss: ~ $14M
Analysis
$14 million was stolen after the Korean cryptocurrency exchange GDAC was hacked.
At 7 a.m. on April 9, the attacker took control of some of the exchange's hot wallets and began transferring cryptocurrency into wallets controlled by the attacker— Korean Standard Time.
As a result of the attack, hackers stole approximately 61 $BTC, 350.5 $ETH, 10 million WEMIX gaming coins, and $220,000 in $USDT. This is equivalent to about $14 million in cryptocurrency.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
Decoding Sentiment Protocol’s $1 Million Exploit
The Sentiment Protocol on the Arbitrum Chain was attacked on April 4th due to a read-only reentrancy vulnerability. The attackers took advantage of this flaw and stole approximately $1 million. Fortunately, the attacker returned around 90% of the funds stolen.
Why is Multi-Party Computation (MPC) Critical for Web3 Security?
The Multi-Party Computation cryptographic protocol is concerned with Privacy-Preserving Technologies. MPC is used by more than one party to arrive at a result or conclusion based on their data so that no party has access to the data of any other party while still serving the purpose. This is accomplished by providing private data fragments to each participating party for them to participate in computing a specific result.