In brief⚡
MEV bots suffered a malicious sandwich attack that cost them around $25 million.
Sentiment Protocol lost ~$1 Million due to read-only re-entrancy vulnerability.
Allbridge suffered a loss of ~$570K due to a price manipulation attack.
Hacks and Scams⚠️
Mev Bots
Amount of Loss: ~ $25M
Analysis
On April 3, MEV bots were subjected to a malicious sandwich attack, which cost them approximately $25 million.
According to data on the chain, the malicious verifier who attacked the MEV bots today was punished by Slash and kicked out of the verifier queue.
The MEV bots were attacked because, even if the beacon block was incorrect, the relay still returned the payload to the proposer, allowing the proposer to access the block's content before another block was finalised.
The attacker used this flaw to maliciously construct an invalid block, preventing the block from being verified and the relay from broadcasting (the status code is 202) in advance to obtain the transaction content.
To address this issue, mev-boost-relay has urgently released a new version, and relay operators are advised to upgrade the relay as soon as possible.
Allbridge
Amount of Loss: ~ $570K
Analysis
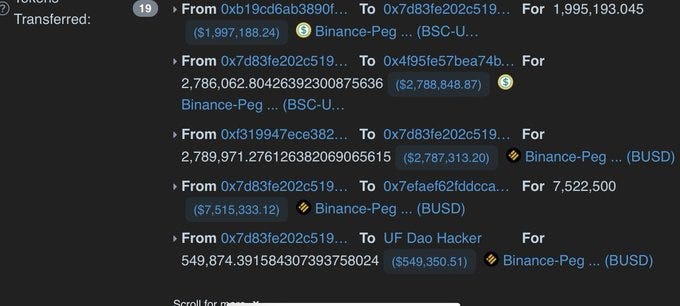
The notorious UF Dao Hacker strikes again, pulling off a masterful heist on Allbridge and escaping with over $550,000.
Attacker flash loans $7.5 million in BUSD, swaps $2 million in BUSD for $2 million in $BSC in pool 0x2c3c, and deposits in pool 0xb19c.
They then deposit $5 million BUSD into pool 0x179a and exchange the remaining $500,000 $BUSD for BSC-USD in pool 0x2c3.
The masterstroke occurs when the attacker exchanges $500K BSC-USD for $BUSD in Allbridge's Bridge contract, securing a high dividend from the previous liquidity deposit.
They quickly remove the BUSD liquidity in 0x179a, disrupting the pool's balance.
Finally, the attacker planned the grand escape he moved 1,700 BNB through Tornado Cash, obscuring their tracks and disappearing with the proceeds.
Sentiment Protocol
Amount of Loss: ~$1M
Analysis
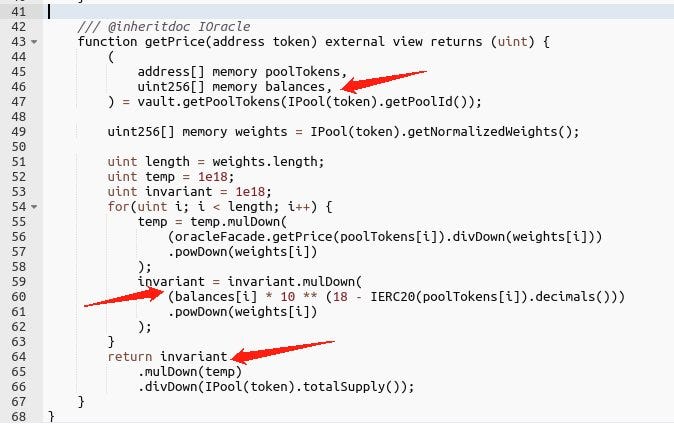
Sentiment Protocol recently experienced a major security breach that resulted in a $1 million loss.
The attacker first uses Balancer Vault's "joinPool" function to make a deposit.
Then he calls "exitPool" to withdraw, during which Balancer Vault sends eth to the attacker to invoke the attack contract's fallback function.
In the fallback function, the attacker invokes the 0x62c5 contract's borrow function, which computes a price based on the Balancer Vault return data.getPoolTokens().
The attacker is currently in the process of "exitPool." The total supply in the pool has been reduced, and the data has not been updated, allowing the attacker to borrow more assets by exploiting the data error.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
5 Common Errors in Solidity Programming Language
Several events in recent months have raised concerns about the security of smart contracts. We were exposed to vulnerabilities, resulting in a massive financial loss as compensation. However, the security of Smart contracts has improved over time. However, we must be cautious and prepared for any potential threat. Most of these attacks are carried out due to a few common vulnerabilities in smart contracts.
Tune in to Engaging Twitter Spaces & Webinars! 🎙️
Web3 Community Spotlight🔦
Cheat the random number generator and become the owner of the contract.