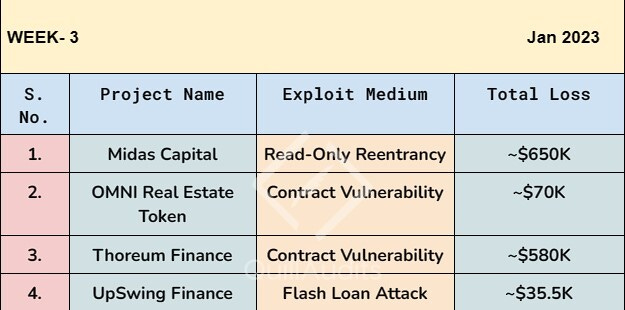
Midas Capital has suffered a loss of ~$650K due to the read-only-reentrancy problem.
HashingBits | Week- 3
In brief⚡
Events Under the Spotlight💥
Midas Capital has suffered a loss of ~$650K due to the read-only-reentrancy
Midas Capital was attacked and exploited in the Polygon liquidity pool of the stablecoin protocol Jarvis and has lost $650,000 due to the read-only-reentrancy problem.
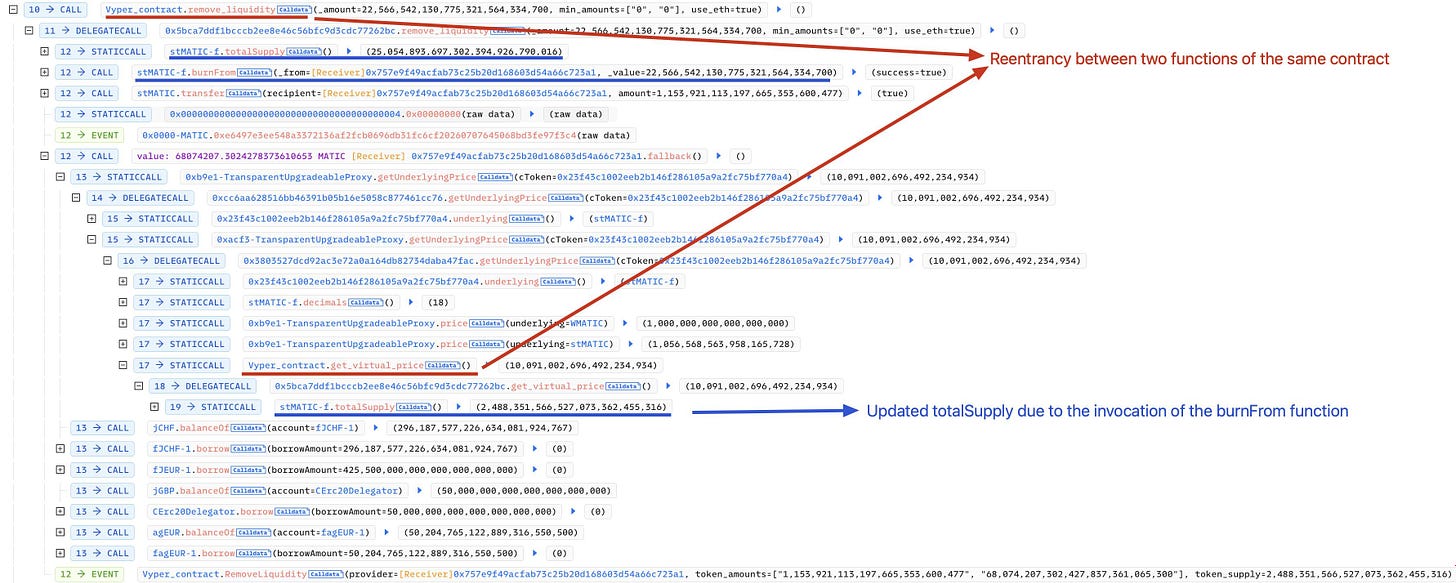
The Midas pool was attacked with read-only reentry. When contract storage is changed using flash loans, this type of attack takes advantage of flaws in view methods that can be called callbacks.
The hacker used Balancer V2, AAVE V3, and AAVE V2 to obtain WMatic flash loans. They then entered the Midas markets and provided some liquidity to Curve (0 stMatic, 270000 of WMatic).
The hacker then deposited Curve LP as collateral to Midas and added a large amount of liquidity (0 stMatic and 71M WMatic), resulting in an imbalanced market.
By removing liquidity from Curve, the hacker triggered a callback that enabled them to borrow jCHF, jEUR, jGBP, and agEUR at an incorrect Curve LP price in Midas, resulting in their collateral being compromised.
OMNI Real-Estate Token Exploit for ~$70K
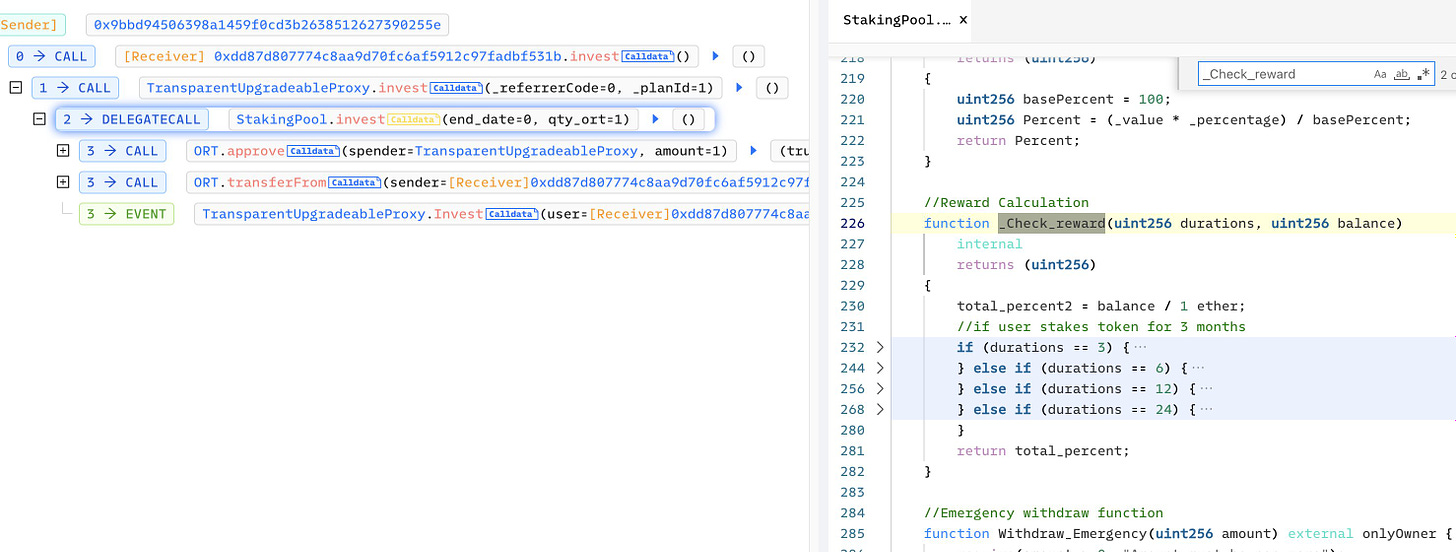
The OMNI Real-Estate Token was abused because the arguments in the StakingPool contract were not sufficiently checked. To claim rewards, the attacker can invest one Wei and withdraw (ORT token)
The _Check reward function computes the reward based on the deposit duration and amount. On the other hand, the duration is derived from the input parameter end date, the value of which is not checked.
If the durations parameter is not valid while in the _Check reward function, a default state variable (total per cent) of 6000e18 is returned at the start of the attack.
FixedFloat provides funding for the attack. The attacker carried out multiple such attacks, and the harvested ORT tokens were exchanged for BNB.
The Thoreum Finance project was compromised, and approximately ~$580K was stolen.
Thoreum Finance got hacked the total loss targeted is approximately 2260 $BNB.
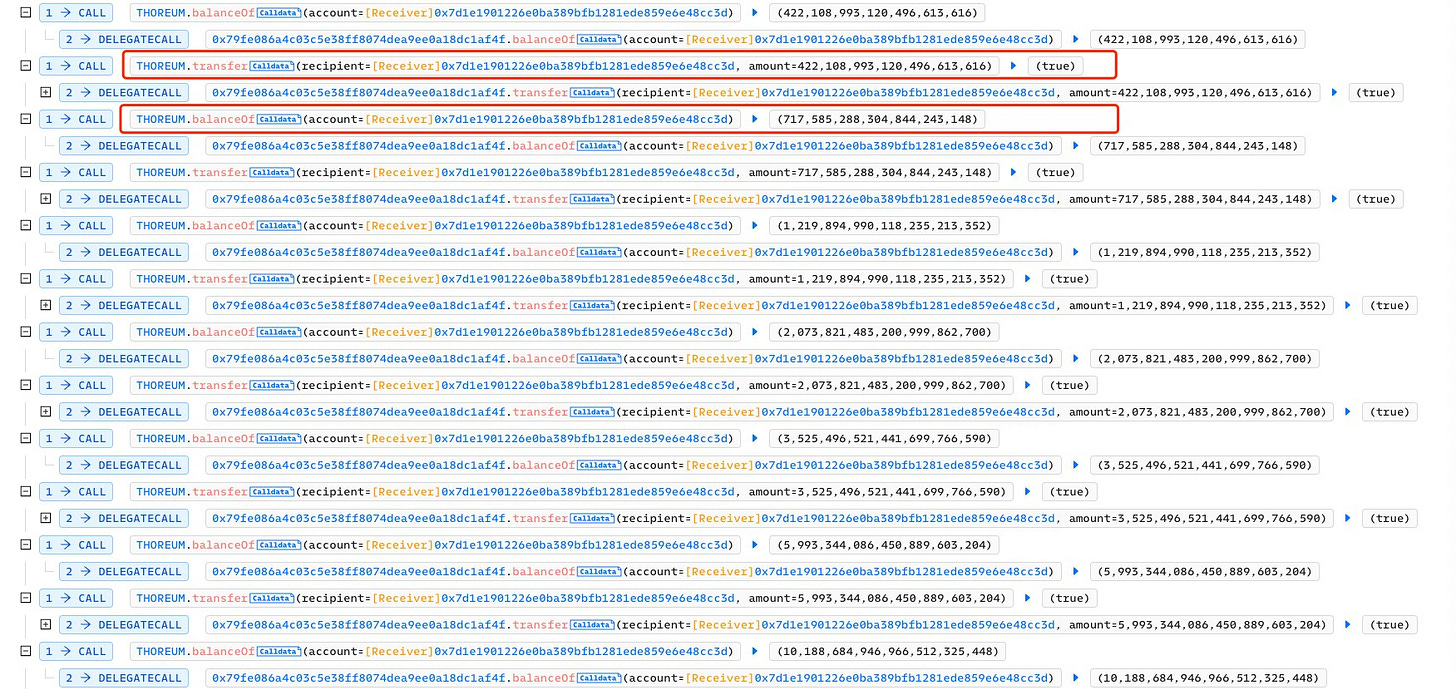
The issue is with how function transfer is implemented. When the receiver is the same as the sender (i.e., 0x7d1e1901226e0ba389bfb1281ede859e6e48cc3d), the sender's token (i.e., $THOREUM) balance increases. The $THOREUM has finally been converted to $BNB.
The token contract is upgraded numerous times quickly, which is suspicious. It is specifically upgraded twice within 4 hours to the vulnerable one (i.e., 0x79fe086a4c03c5e38ff8074dea9ee0a18dc1af4f). The deployer's private key may have been compromised.
Due to a suspected vulnerability in the transfer function of the unsourced contract 0x79fe created by the ThoreumFinance project team, when the from and to addresses of the transfer function is the same, the balance will multiply, resulting in a transfer to themselves and the attacker repeats the operation many times, eventually making a profit of 2000BNB.
A flash loan attack on UpswingFinance resulted in the loss of ~22 ETH (~$35.5K)
A flash loan attack on Upswing Finance resulted in a loss of 22 ETH ($35.5K). Since October 2020, the project has been inactive due to price manipulation.
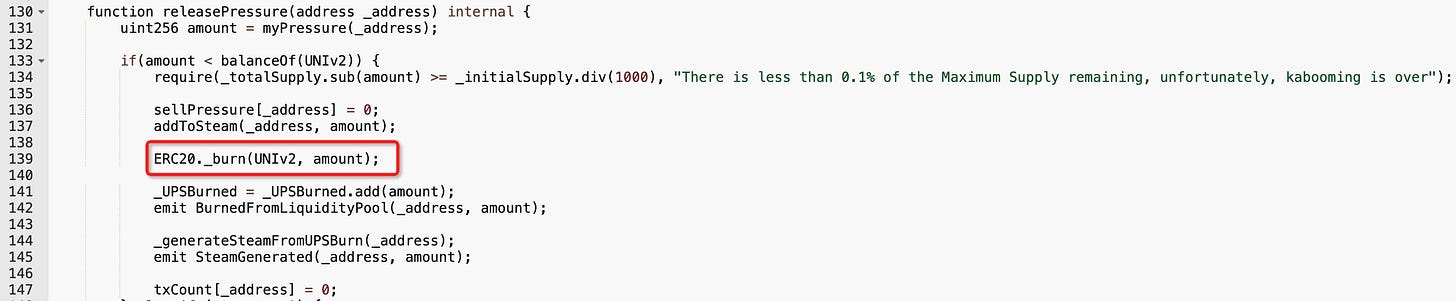
It is a price manipulation attack caused by a design flaw in the $UPStkn token's _transfer function. The amount will be accumulated if the receiver is a UNI pool.
The total amount will be checked. In a specific case, a certain number of tokens will be burned from the pool to manipulate the pool price and drain the WETH.
The attacker employs 18 swaps to increase UPStkn's sell pressure. During the swaps, the attacker also exchanges 1.31 Ether for 136,299.97 UPStkn.
The attacker sends zero UPStkn to himself to trigger the internal function release. The pressure further burns the pool's 573,300.39 UPStkn, raising the price of the UPStkn.
The attacker manipulates the price of the 136,299.97 UPStkn and sells it for 24.877 Ether.