In brief ⚡
Orbit Chain's Ethereum Bridge Hacked on New Year's Eve, Losing $81.5M to Compromised Multisig: Links to Lazarus Group Raise Concerns.
Radiant Capital, Aave V2 Fork, Loses $4.5M to Flash Loan Exploit on Arbitrum's New USDC Market.
Arbitrum-Based Gamma Strategies Exploited for $4.5M: Flash Loans and Configuration Flaws Exposed.
Hacks and Scams⚠️
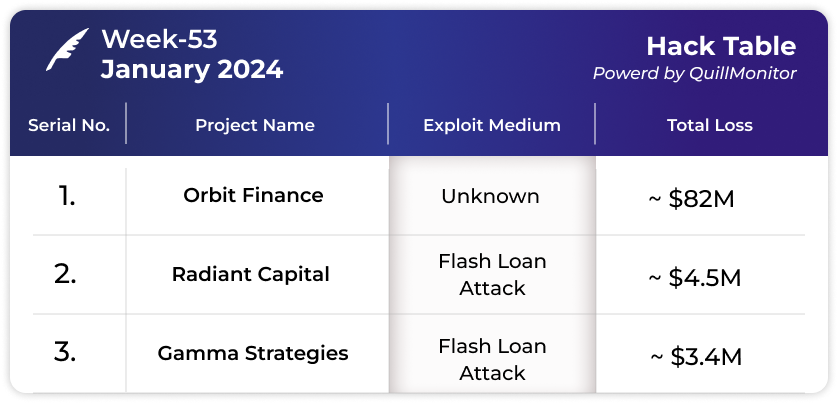
Orbit Chain
Amount of Loss: ~ $82 M
Analysis
On New Year's Eve 2023, Orbit Chain's Ethereum bridge suffered a significant loss of $81.5 million due to a compromised multisig.
Orbit Chain, distinct from Orbiter, is a standalone network designed to act as a hub between various established ecosystems.
The breach occurred just after 9 PM UTC, and the compromised access to Orbit Bridge was officially confirmed around 8:52:47 PM +UTC on the same day.
The attack involved withdrawals of various cryptocurrencies, including 10M DAI, 231 WBTC ($9.8M), 9500 ETH ($21.5M), 10M USDC, and 30M USDT. The bridge was deactivated at 22:21 UTC.
The attacker's primary address, 0x9263e7873613ddc598a701709875634819176aff, is linked to Lazarus, a group responsible for significant losses in 2023, including attacks on projects like Belt and Klayswap.
Over half of Orbit Bridge's Total Value Locked (TVL) was drained in the attack, contributing to Lazarus' already substantial losses of at least $250M in 2023.
Radiant Capital
Amount of Loss: ~ $4.5M
Analysis
Radiant Capital, a lending protocol forked from Aave V2, lost 1900 ETH (approx. $4.5M) due to a known bug affecting newly-launched markets on Arbitrum.
The hack occurred on the Arbitrum deployment's new native USDC market, with the attacker exploiting a vulnerability in Aave-forks code affecting recently-launched and empty markets.
The attacker, who deployed the attack contract just six seconds after the market activation, likely identified the vulnerability through updates to the Aave protocol itself.
The bug involves a brief window after launch where a flash loan can manipulate collateral value due to a rounding error and a totalSupply value of 0 in the forked Aave V2 code.
The original Aave protocol had mitigated this issue by requiring an initial deposit with the creation of new markets to prevent them from being empty.
Although an official confirmation stated that no current funds are at risk, the $4.5M already stolen remains unrecovered. The Radiant Team has communicated with the hacker, expressing confidence that they are dealing with a whitehat for various reasons.
Gamma Strategies
Amount of Loss: ~ $4.5M
Analysis
Gamma Strategies, an Arbitrum-based liquidity management protocol, was exploited for at least $4.5M.
Initially mistaken for CryptoAlgebra, the victim was later correctly identified as Gamma.
The attack, utilizing flash loans, manipulated deposit values to mint an inflated number of LP tokens.
Gamma paused deposits, acknowledging the hack and attributing it to high price change thresholds in certain vaults.
Despite three 2021 incidents, Gamma rebranded from Visor Finance, claiming no original developers or founders remained.
The exploit, unrelated to previous audits, highlights ongoing vulnerabilities in DeFi protocols in 2024.
Explore the Depths of Knowledge: Research Papers, Blogs and Tweets🔖
Tweets
GitHub Repos
Articles
An Open Letter to the Manufacturers and Designers of Crypto Wallets
What should I use to store my Cryptocurrency? | Web3 Wallet Guide
Web3 Community Spotlight🔦
Note - all the respective links has been embedded in the image
Thanks for reading HashingBits! Share a summary of our newsletter on your social media platforms, tag us, and use the #AwareToEarn hashtag, and you could win 10 USDT as a reward! Help us build a safer Web3 ecosystem and have a chance to earn rewards and support our work.