In brief⚡
Events Under the Spotlight💥
Cross-chain DEX Aggregator Transit Swap was Hacked
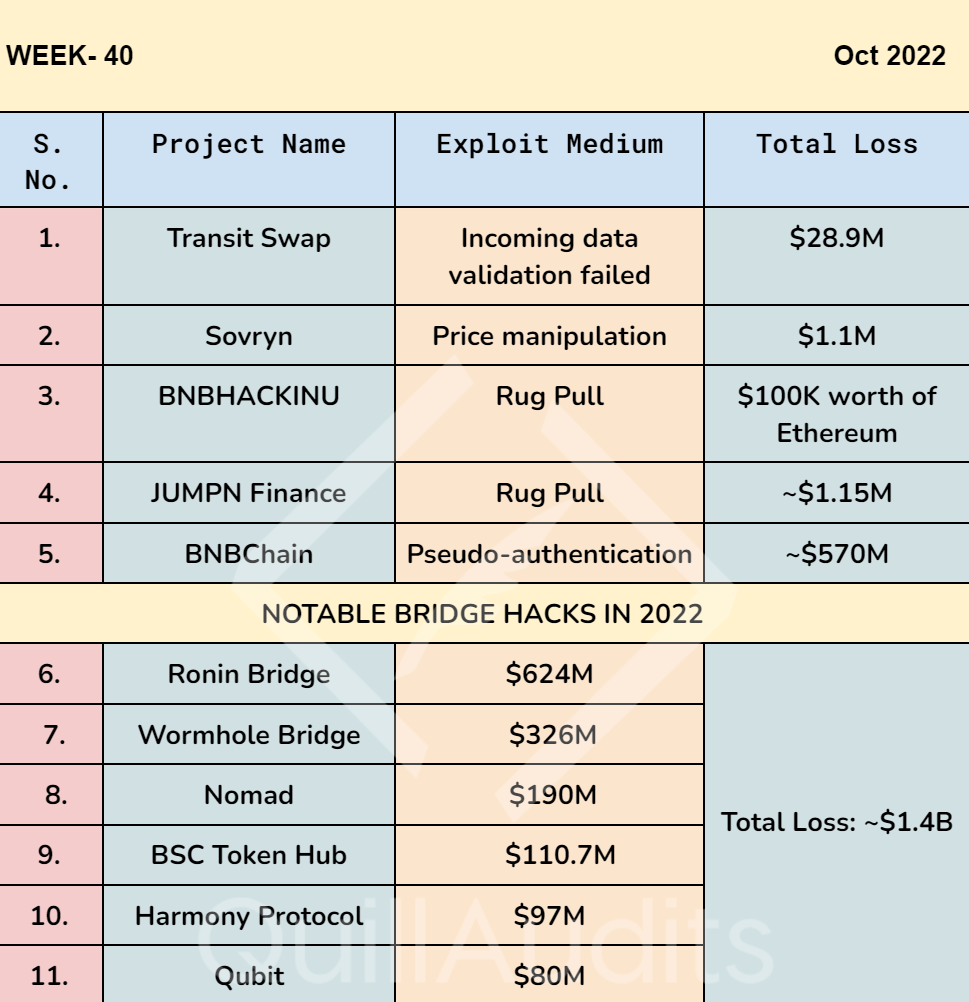
Decentralized cross-chain exchange Transit Swap was hacked on Sunday and reported that some US $28.9 million worth of tokens were stolen.
The hackers returned 65% of the stolen token value on Monday, amounting to about US $18.9 million.💰
Bitcoin DeFi Protocol Sovryn suffered $1.1 million Exploit
Bitcoin-based decentralized finance protocol Sovryn suffered a major exploit on Tuesday, with a hacker draining $1.1 million from the protocol.
The hacker exploited a legacy function to drain the protocol, using a price manipulation technique in one of the protocol’s lending pools.
Interim Exploit Update by Sovryn🚩
~$570M worth of Binance’s BNB token was hacked
According to the blog post, hackers withdrew approximately $570 million worth of BNB tokens from BNB Chain on Friday.
The company previously estimated that the total amount withdrawn would be in the range of $100 million to $110 million.
After hackers stole around $570 million worth of Binance’s BNB token, the cryptocurrency exchange temporarily suspended its blockchain network.
The Root Cause of the hack lies in this line.⚠️
To fix this, the code should be updated from-
`if !bytes.Equal(derivedRoot, lpath.Right) ...`
to something like:
```
expectedHash := lpath.Left
if len(lpath.Left) == 0 {
expectedHash = lpath.Right
}
if !bytes.Equal(derivedRoot, expectedHash) ...
```
This will ensure that the hash stored in the inner node matches the hash calculated throughout the path. (If the path node has a "Left," that node's hash is combined with the hash of the other branch; otherwise, the "Right" is hashed.) - See💡
The bug, as also exploited in @samczsun's PoC, is that one can go to any node in the proof path and add a `Right` hash (that verifies a forged, planted subtree).
The code ignores this hash in the computation of the topmost root hash because the node already has a `Left` hash.
The identical problem, in which proof path nodes with both "Left" and "Right" are treated incorrectly or rejected, may occur elsewhere in the code.👾
This needs some thought.
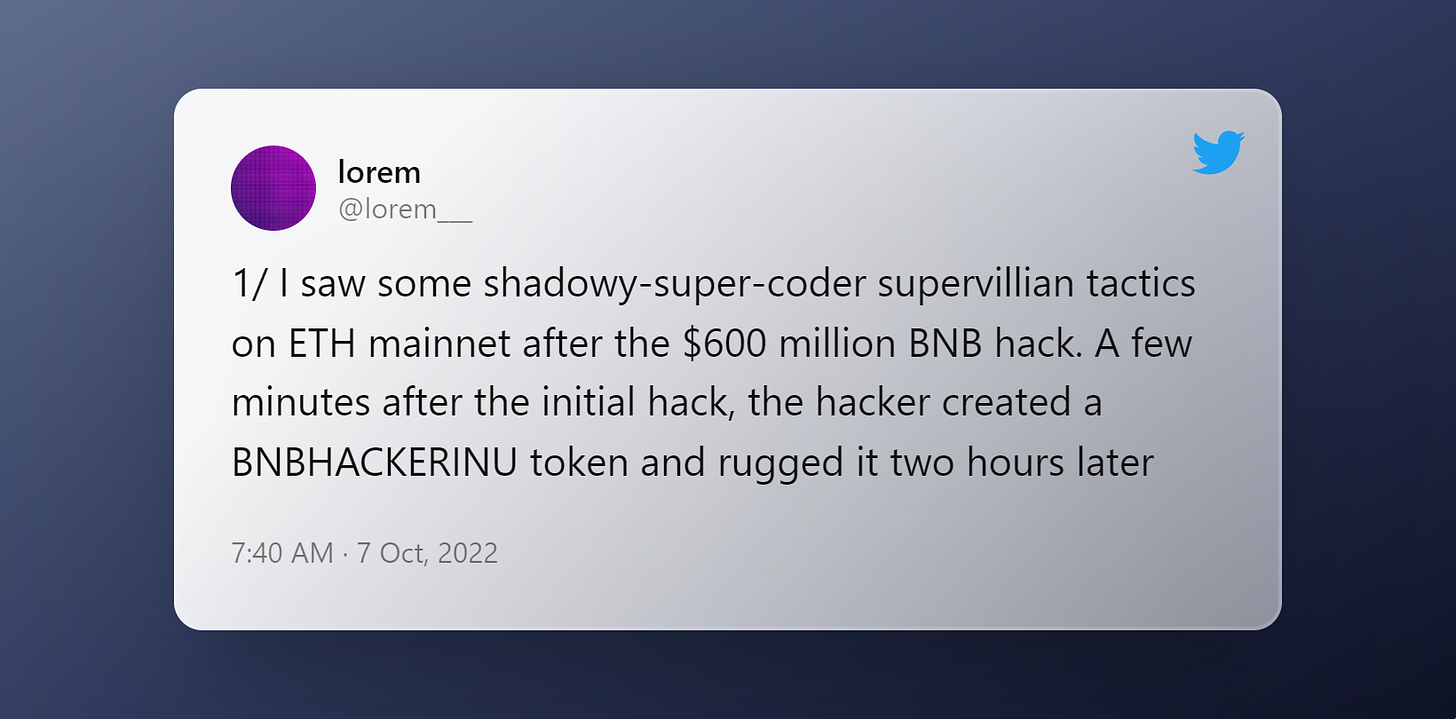
After the ~$600 Million BNB Hack, Ethereum Experiences Rug Pull Attacks
BNBHACKINU – a token created in a clear reference to both the recent BNB Chain hack and popular dog-themed memecoins – becomes the latest scam that perpetrators pulled off to steal crypto.
A malicious actor created fake tokens after the initial hack on BNB.
The address of the token deployer does not match that of the initial hacker of BNB Chain. 🚩
However, the lead deployer variable in the contract does have the address matching the BNB hacker.
Lorem highlights how the entire smart contract had a malicious code structure.
Firstly, the malicious actor had a function that allowed him to create an arbitrary number of tokens.
More importantly, three functions of the smart contract allowed the hacker to transfer any holder’s token back to another account without any permission.
The hacker was able to rug out close to $100K worth of Ethereum.💰
He then repeated the same tactics with a new token called HACKERSHIBA.
JUMPN Finance siphoned off ~$1.15M in a Rug Pull Scam
JUMPN Finance $JST rugged with ~$1.15M.
2,100 $BNB sent to Tornado Cash; 2,058 $BNB sit at hacker's address.
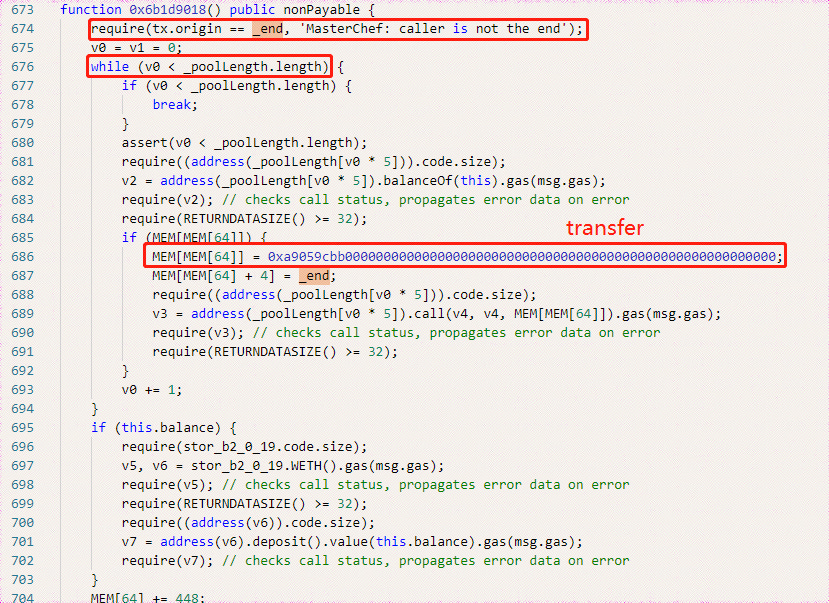
The scammer calls the 0xe156 contract’s 0x6b1d9018() function and withdraws the user assets and transfers to the scammer's address.