🤐 OpenZeppelin disclosed an Address Spoofing attack - multiple tokens rekt
HashingBits | Week- 49
In brief ⚡
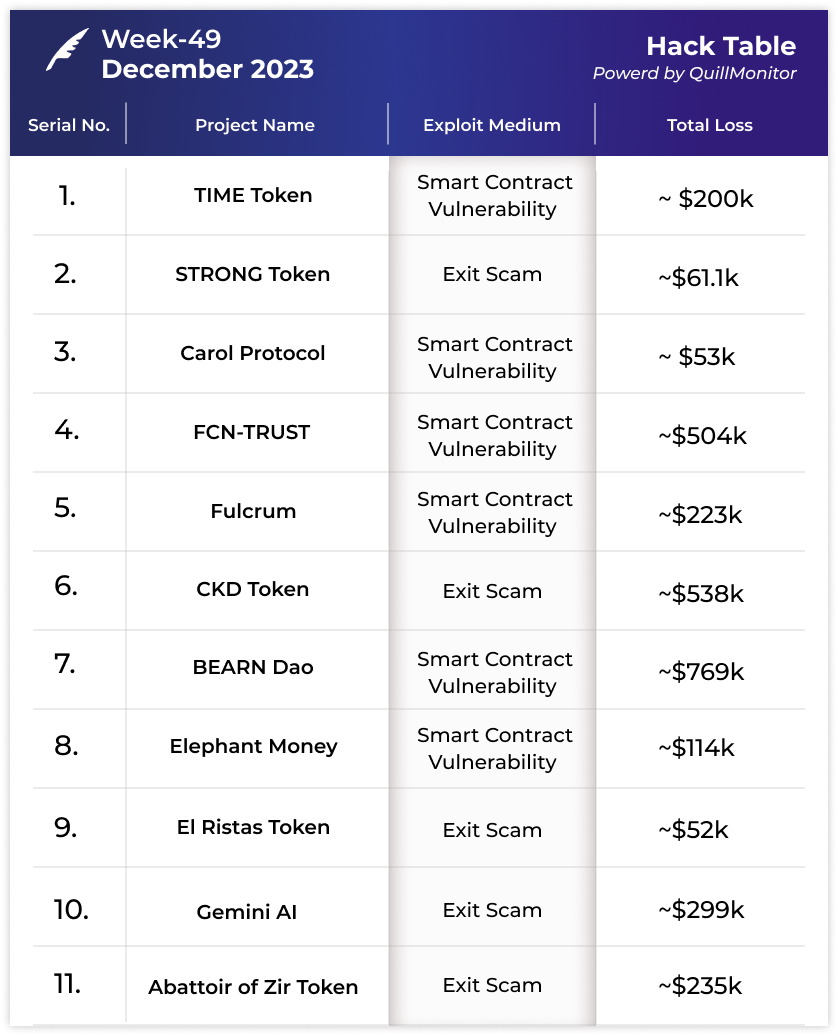
TIME Token Hack: $200K Lost in Decentralized Exchange Exploit Due to Forwarder Smart Contract Vulnerability
STRONG Token Scandal: Over $61K Vanishes in Exit Scam Linked to Lucky Star Hack
CKD Token Rugged for $538K: Deployer and Associates Drain Liquidity in Multiple Transactions
BEARN DAO Exploited for $769K: ConvertDustToEarned Function Vulnerability Leads to Major Loss
FCN Trust Flash Loan Attack: Over $504K Lost, Causing 99% Token Price Crash
Carol Protocol Compromised: Flash Loan Attack Causes $53K Loss Through Stake Manipulation.
Fulcrum Platform Hacked: Over 99 ETH ($223K) Stolen Amidst Security Concerns in Inactive Protocols
Gemini AI Token Plummets: $299K Lost in Major Transaction, Token Value Drops by 99.58%
Abattoir of Zir Token Plunge: $235K Lost as $DIABLO Token Value Hits Zero
El Risitas Token Falls: $52K Lost in 100% Value Drop, Major WBNB Swap Recorded
Elephant Money Treasury Hacked: $114K Stolen Due to Lack of Slippage Protection in Swap Function
Hacks and Scams⚠️
TIME Token
Amount of Loss: ~ $200k
Analysis
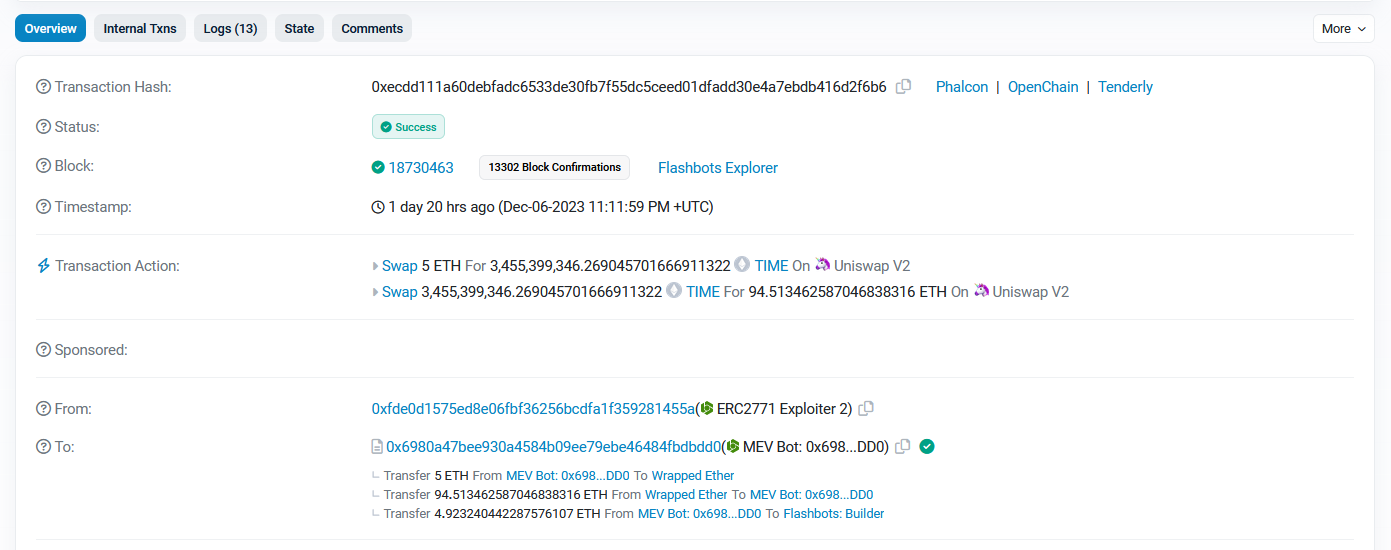
Exploit on Dec 7 involving the TIME token on a decentralized exchange (DEX)
Resulted in a loss of about 94 ETH, equivalent to approximately $200,000
Orchestrated through a vulnerability in the Forwarder smart contract
Forwarder smart contract is intended to execute transactions from arbitrary sender addresses
Exploit executed through a critical vulnerability related to the inconsistency between two functions: Forwarder.execute() and TokenERC20.multicall()
STRONG Token
Amount of Loss: ~ $61.1k
Analysis
SAI pro token on BNB chain was exploited for over 1.7 Million usd.
It was an exit scam and the deployer swapped the funds over multiple transactions
This address has also been found to be involved in Lucky Star hack.
CKD Token
Amount of Loss: ~ $538k
Analysis
On Dec 5, the CKD token on bsc was rugged for $539K when the deployer and other EOA removed the liquidity and dumped the tokens.
The deployer removed liquidity in over 3 txns:
0xa9b929f980b946a17c1b424a2fb13e761a675540b7470c451b803abcdc476462
0x1f36b29931484d55b6b71a52d6bffd249b0b8fe66f765550a7bbdfb8c52a0b78
0xe6fa778eceeb98dbd5d9c165cc90472b8518dae396baa84ded5a9199390354f6
BEARN Dao
Amount of Loss: ~ $769k
Analysis
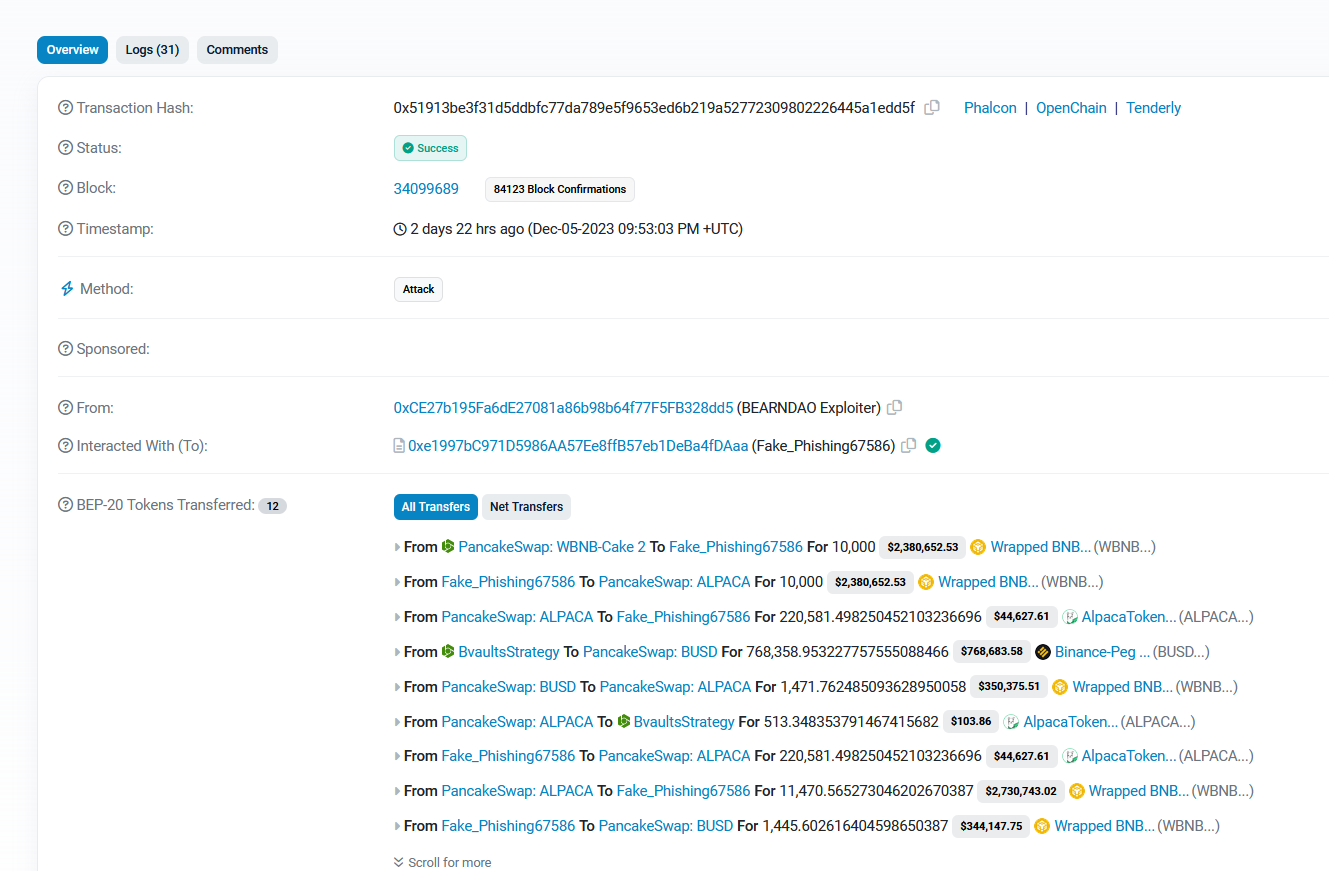
On December 5th, BEARNDAO, a decentralized reserve currency protocol on BSC, suffered an exploitation incident amounting to approximately $769K.
The exploit was facilitated through a vulnerability in the ConvertDustToEarned() function within the BvaultsStrategy SmartContract.
The attacker employed a sandwich attack strategy by leveraging the bug in the aforementioned function.
Specifically, the attacker established a malicious contract designed to execute the exploit and carry out the attack.
FCN Trust
Amount of Loss: ~ $504k
Analysis
On December 1, the FCN-TRUST (FCN) token on Binance Smart Chain (BSC) experienced a flash loan attack, leading to a loss of over $504k.
The attacker exploited a vulnerability in a specific unverified contract (0x431abb) on the BSC network.
The attack caused a drastic 99% crash in the token price within a few hours.
The unverified contract, 0x431abb, displayed flaws in its reward calculation logic, resulting in a loss exceeding $500,000.
The contract's primary function was to distribute FCN token rewards to users based on the reserve amount of the FCN-BSC-USD pair.
Carol Protocol
Amount of Loss: ~ $53k
Analysis
Carolprotocol fell victim to a protocol exploit, triggered by a flash loan attack.
The exploit was instigated by manipulating the stake amount, which served as the root cause.
The financial impact of the attack amounted to $53,000.
Contract Address - https://basescan.org/address/0x26fe408bbd7a490feb056da8e2d1e007938e5685
Fulcrum
Amount of Loss: ~ $223k
Analysis
Fulcrum, an inactive margin protocol, experienced a hack resulting in a loss of over 99 ETH.
Ancilia, a Web3 network security firm, identified and reported the attack on Fulcrum.
The hacker left a message in French on-chain, translating to 'Steal the body, negotiate with the ghosts.'
Fulcrum, initiated in June 2019, has ceased updates, and its website is inaccessible.
The developer, bZx, discontinued platform updates beyond 2020.
The hack raises concerns about security vulnerabilities in dormant protocols.
Over 99 ETH was the value compromised in the Fulcrum hack.
Ancilia's detection highlights the importance of proactive network security.
The French message left by the hacker adds an eerie and mysterious dimension to the breach.
The incident emphasizes the risks associated with inactive or unsupported platforms in the crypto space.
Gemini AI
Amount of Loss: ~ $299k
Analysis
Gemini Ai's $Gemini token has witnessed a staggering decline of -99.58% in its value.
A transaction involving the address 0x6Caa...3129 took place, swapping a massive 4,248,342,655,043,365.9 $GEMINI for 133.97 $WETH, equivalent to approximately $299.7K.
Abattoir of Zir Token
Amount of Loss: ~ $235k
Analysis
Abattoir of Zir $DIABLO has experienced a 100% drop.
The address 0x1a59...74dB has swapped 785,402,593,664.14 $DIABLO for 104.73 $WETH, equivalent to approximately $235.5K.
El Risitas Token
Amount of Loss: ~ $52k
Analysis
EI Risitas $KEK has undergone a 100% drop in value.
The address 0xFb42...769D executed a swap of 2,200,000,000,000,000 $KEK tokens for 227.02 $WBNB, equivalent to approximately $52.6K.
Elephant Money
Amount of Loss: ~ $114k
Analysis
Elephant Money Treasury, ElephantStatus, was recently hacked for $114k.
The vulnerability that led to the hack is the same as another incident involving BEARNDAO on the same day: lack of slippage protection on swap.
The hacker targeted an unverified contract deployed by Elephant Money, which had privileges to withdraw funds from the treasury.
The hacker utilized the sweep() function to force the contract to withdraw funds and execute a swap without slippage protection.
The distinction between the two hacks lies in the fact that the hacker exploited an unverified contract with withdrawal privileges in the case of Elephant Money.
Explore the Depths of Knowledge: Research Papers, Blogs and Tweets🔖
Tweets
GitHub Repos
Articles
MEV Bots 101: What are MEV Bots and How are They Making Millions?
Becoming a web 3 security researcher: Balancing foundations and the attacker mindset.
Web3 Community Spotlight🔦
Note - all the respective links has been embedded in the image
QuillCon Codequest came to an end.
Thanks for reading HashingBits! Share a summary of our newsletter on your social media platforms, tag us, and use the #AwareToEarn hashtag, and you could win 10 USDT as a reward! Help us build a safer Web3 ecosystem and have a chance to earn rewards and support our work.