In brief⚡
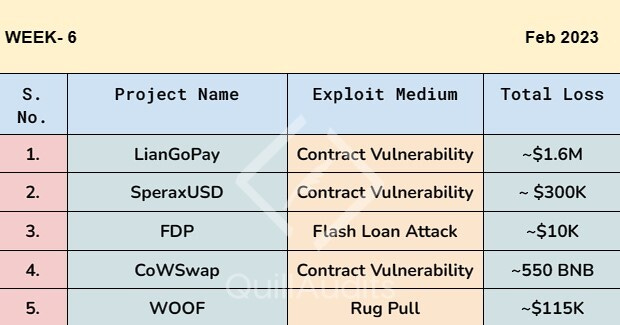
The LianGoPay project lost ~1.6M due to a contract vulnerability that allowed hackers to exploit its poll by leveraging fake LP staking pools.
Hacker exploits SperaxUSD, the Arbitrum ecological stablecoin protocol.
In a flash loan attack, FDP lost ~$10K.
Using the 'solver' exploits, the CoWSwap hacker milks over 550 BNB.
BSC-WBNB-WOOF trading pair rugged for ~$115,000.
Hacks and Scams⚠️
LianGoPay
Amount of Loss: ~$1.6 Million
Analysis
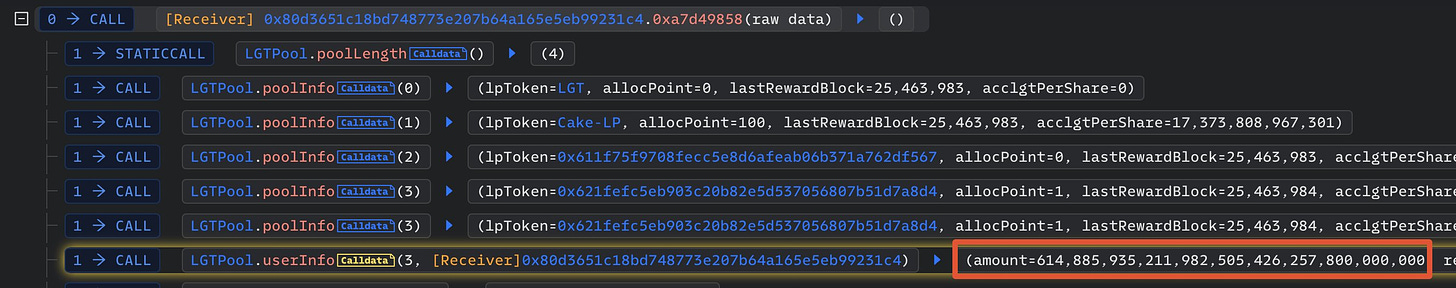
The LianGoPay project announced on February 7 that its assets in the LGTPool pledge contract on the BNB Chain had been stolen, resulting in a loss of approximately 1.6 million US dollars.
The coin thieves had spent a long time preparing for the theft. The thief's address received gas fees from Tornado Cash 58 days before the incident and deployed the counterfeit LP contract 32 days before the incident.
The owner administrator of LGTPool created a fake LP token pledge pool (Pool No. 3). Then the thief put a large amount of LP tokens into the pool for the pledge, obtaining 6.14 million pieces of LGT reward token, according to analysis.
SperaxUSD
Amount of Loss: ~$300K
Analysis
SperaxUSD, the Arbitrum ecological stablecoin protocol, tweeted that an attacker increased the token balance of his address to 9.7 billion without providing the corresponding collateral and that approximately $300,000 was liquidated.
The Sperax team has discovered the exploiter's accounts on CEXs and is taking action against him. On February 4, 03:11 AM UTC, all $USD transactions and the smart contract were blocked.
The Sperax team will recapitalize the liquidated amount before relaunching the protocol.
FDP Token
Amount of Loss: ~$10K
Analysis
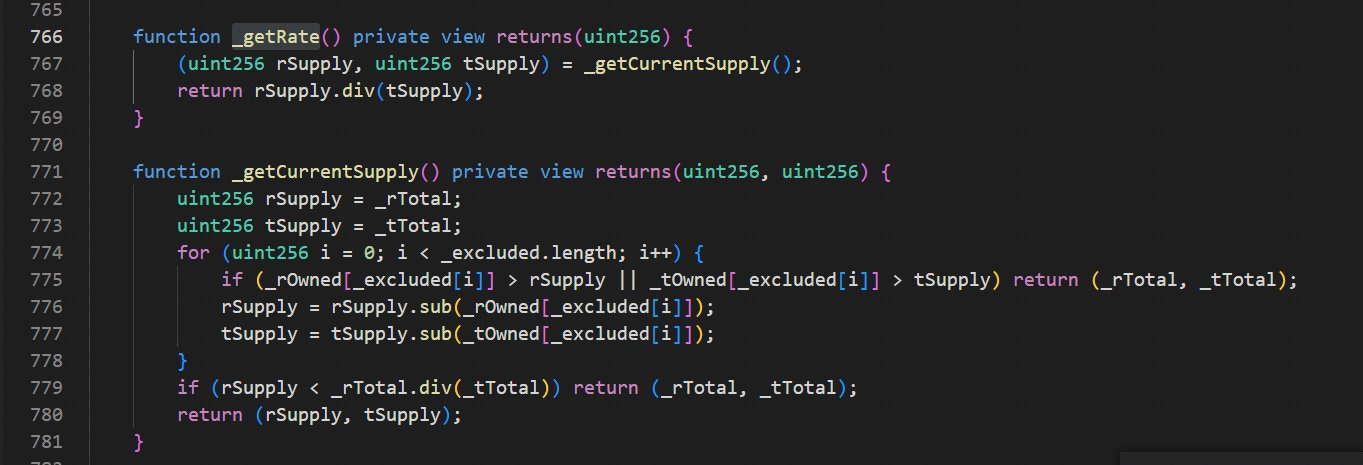
FDP lost $10,000 in a flash loan attack. The attacker borrows 1,363 WBNBs and exchanges 16 for 284631626035854 $FDP.
Before the manipulation, currentRate calculates the FDPs. rtotal is not reduced in this case, and neither the pair nor the attacker is a deflationary exception.
The attacker calls the deliver function with the tAmount, which reduces the user-specified tAmount and adds it to the fee. The 284631626035854 tAmount FDPs account for 28% of the total supply of FDPs.
When _rTotal is 28% less and _tTotal remains the same after calling deliver, _getRate shrinks. Because the transaction pair is not a deflation-excluded address, the obtained balance is larger. The attacker can withdraw the increased $FDP and exchange it for $WBNB.
CoWSwap
Amount of Loss: ~550 BNB
Analysis
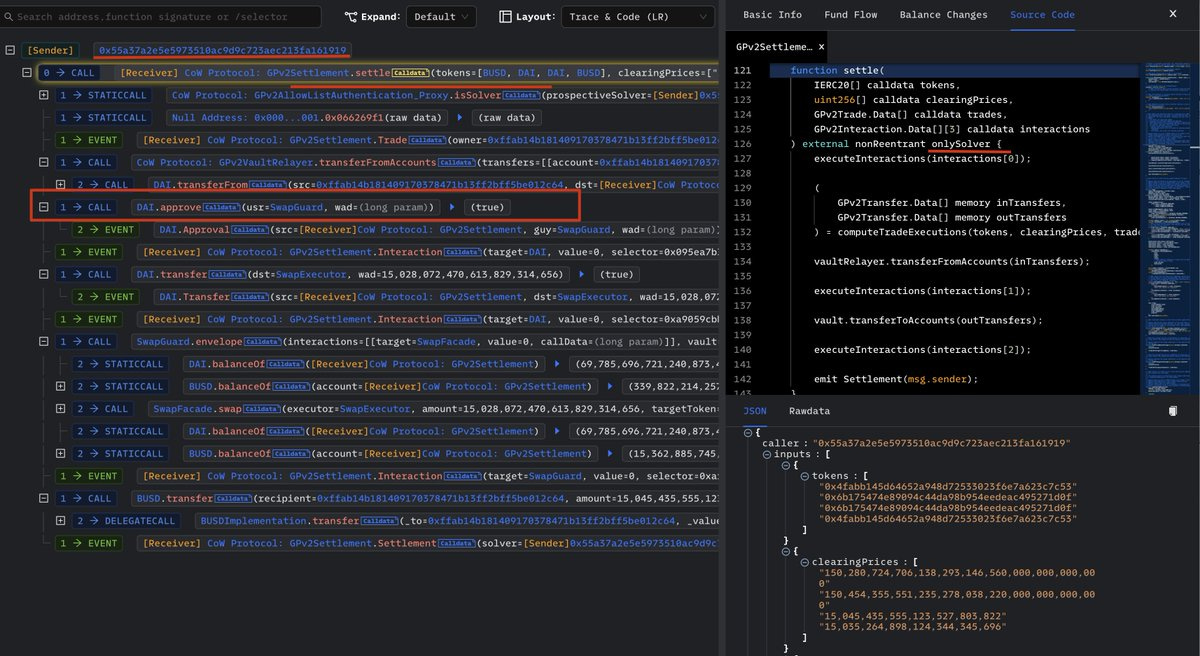
The decentralised exchange (DEX) protocol CoW Swap recently suffered an attack, losing more than 550 BNB as its GPv2Settlement contract, which authorised fund transfers from the protocol, was exploited.
A multisig added a wallet address as a "solver" of CoW Swap. The address then initiated the transaction to approve DAI to SwapGuard, causing SwapGuard to transfer DAI from the CoW Swap settlement contract to other addresses.
According to CoW Swap, the exploited settlement contract has access to only the fees collected by the protocol in a week. The team stated that it could only access user funds with an order directly signed by users.
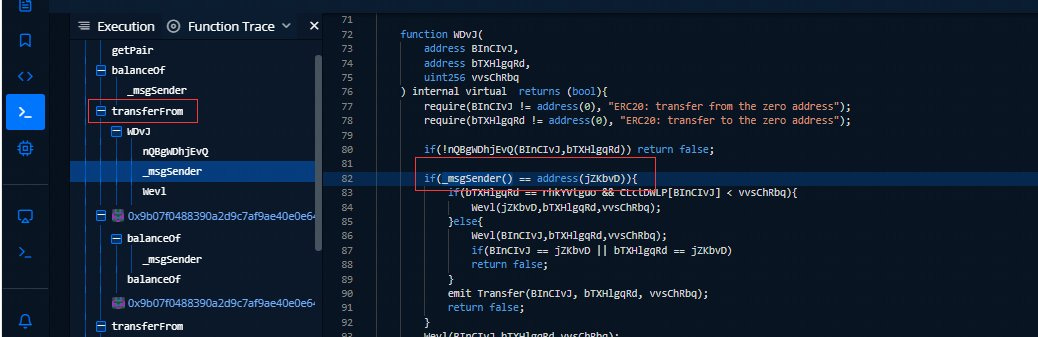
BSC-WBNB-WOOF Trading Pair
Amount of Loss: ~$155K
Analysis
The BSC-WBNB-WOOF trading pair was acquired for $115,000 via a backdoor. Due to the exploit, the price of $WOOF has dropped by -88%.
The address (jZKbvD) can transfer WOOF from any address using the transferFrom function to 0 authorization. The attacker transferred $WOOF and updated the pool's reserves before swapping out the WBNBs in the pair with many $WOOF tokens.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
Maximizing DAO Security: An Expert’s Guide to Auditing the Social Layer
DAO exploits have the potential to wipe out millions of dollars. Learn about common ways malicious users can break DAO and how to avoid it.
A Brief on Ethereum Smart Contract Audit
DeFi platforms are vulnerable to various hacks and exploits; learn more about ethereum smart contract auditing and potential threats.
Detecting Malicious Packages and How They Obfuscate Their Malicious Code
Let's now learn about attackers' other, more subtle interests when creating a malicious package: hiding malicious code and finally demonstrating how malicious packets can be detected and prevented.
Tune in to Engaging Twitter Spaces & Webinars!🎙️
Web3 Community Spotlight🔦
Understanding the Sybil attacks in the blockchain


QuillCTF Challange GATE is Live for Builders to flex their coding muscles


Innovations Unleashed: Stay Up-to-Date with Latest Product Launches🚀
QuillAduits launched Hackerboard: Get statistics and in-depth analysis of recent crypto hacks, vulnerabilities, and attack vectors from all over the web3.