In brief⚡
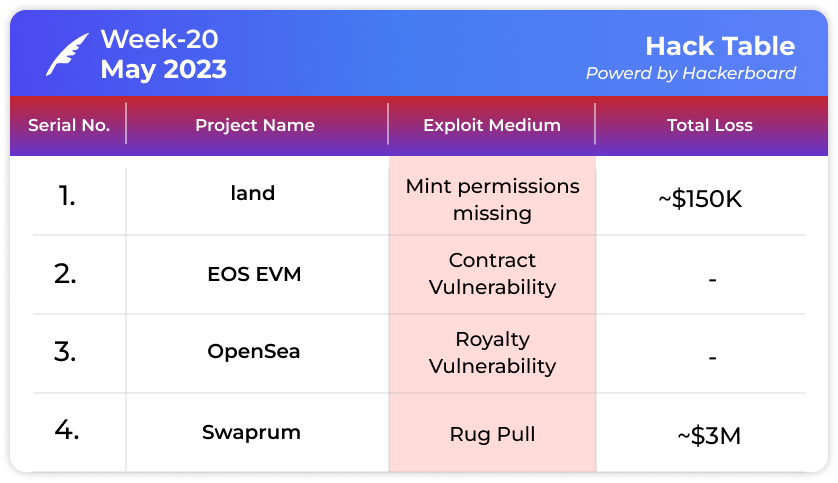
A contract vulnerability caused Land a loss of ~$150K
EOS EVM smart contract got exploited
A vulnerability related to Royalty discovered in OpeanSea
Swaprum lost ~$3M to a rug pull.
Hacks and Scams⚠️
Land
Amount of Loss: ~ $150K
Analysis
The DeFi protocol land was suspected of being attacked and suffered a loss of approximately $150,000 USD.
The attack was carried out due to a lack of mint permission control.
Several miner addresses in the project, including
0x2e599883715d2f92468fa5ae3f9aab4e930e3ac7, can mint NFTs.The attacker instructs the contract
0x2e599883715d2f92468fa5ae3f9aab4e930e3ac7to mint 200 NFTs.The attacker uses the previously minted NFTs to call the
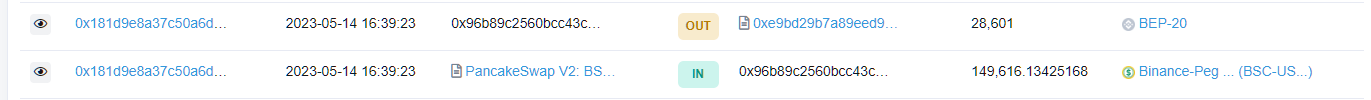
0x2c672a34function of the0xeab03ad7ea0ac5afb272b592bef88cf93ed190c5contract to swap for a large amount of $XQJ (200 $XQJ per NFT).The assailant exchanges 28,601 $XQJ for 149,616 $BUSD.
The attacker continued to mint NFTs until the NFT issue limit was reached.
EOS EVM
Analysis
The EOS Network Foundation announced on Twitter that the EOS EVM had been updated to version v0.4.2, which addresses a serious security vulnerability discovered in the EOS EVM.
The security flaw is related to the state objects tracking the trustless bridge's reserved addresses and how they were not properly undone when an EVM execution context was reverted.
If exploited, it could allow an attacker to illegally drain all of the EOS EVM Contract's stored EOS across the trustless bridge.
All EOS EVM contracts, EOS EVM nodes, and EOS EVM RPC components used by the EOS mainnet must be upgraded.
The patch for the security flaw is in the silkworm engine, which the EOS EVM Contract and the EOS EVM Node share. To ensure consistency between the two components, the patched EOS EVM Node must be deployed alongside the updated EOS EVM Contract.
OpenSea
Analysis
OpenSea is thought to have a royalty loophole.
OpenSea appears to have recently changed the owner's identification standard, meaning NFT projects can no longer set or change royalties. This is a critical error.
It's only been around for two days.
Swaprum
Amount of Loss: ~ $3M
Analysis
Swaprum on Arbitrum rugged costs $3 million.
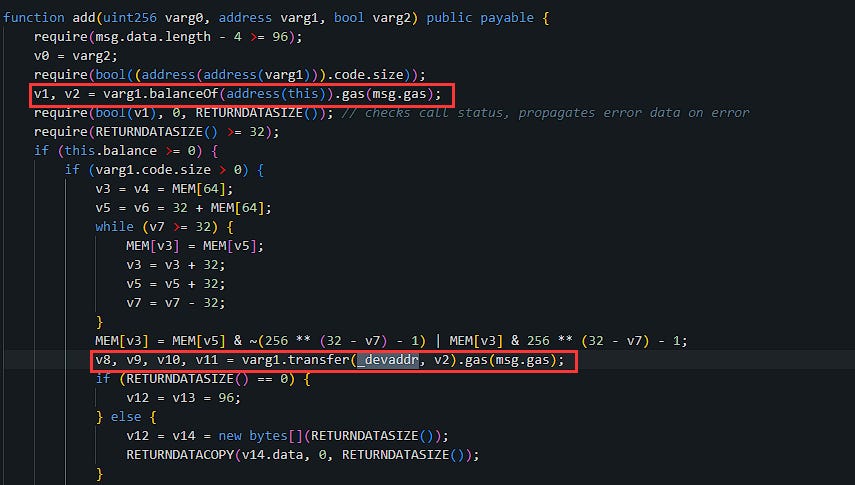
The Swaprum deployer used the
add()backdoor function to steal LP tokens staked by users, then profitably removed liquidity from the pool.The project has upgraded the standard liquidity collateral reward contract to include backdoor functions.
The
add()backdoor function will send LP tokens from the contract to the_devaddaddress. It will return the 'Swaprum: Deployer' address if you query the_devaddaddress.The Swaprum: Deployer removes liquidity using the stolen LP tokens from the previous step.
1,620 $ETH has already been transferred to Tornado Cash.
Explore the Depths of Knowledge: Research Papers & Blogs🔖
TLDR: NFT Security Audits, Risks, and Safety Measures
NFTs on the blockchain are difficult to hack, although not impossible. If not for that, news on NFT hacks wouldn’t be showing up now and then. That’s why it is important to talk about the vulnerability aspects and work on ways of resolving them to make the NFT space bigger and better.
Decoding Deus DAO $6.5 Million Exploit
Due to a smart contract vulnerability, the Deus DAO Protocol was exploited on the Arbitrum, Ethereum, and BNB chains on May 6, 2023. The hackers stole approximately $6.5 million in this exploit.
Web3 Community Spotlight🔦
CTFland's very popular and trusted "Router" protocol is on the hunt for some promising developers.
At CTFland, it is an honour to work at big protocols like "Router protocol"; thus, every citizen is looking to take part in the recruitment challenge.
This time you are fully confident to pull this through; the problem statement is to write a smart contract which takes 2 inputs and returns 1 if the input is equal; otherwise, return a different number.
The challenge may seem easy, but it is for one of the reputed protocols, so there may or may not be some, give it your best and secure that job.